What You See Is What You Encrypt.
The trend of installing malware on corporate networks through the Remote Desktop Protocol is booming among cybercriminals. In the last few months we have analyzed several cases of ransomware attacks directed at companies from different European countries that share this methodology and are being perpetrated by the same attackers.
Once credentials are obtained through a brute force attack on the RDP, the cybercriminals gain access to the computer.
At this point, when the goal is to deploy ransomware, attackers simply execute the corresponding malware automatically to start encryption and ultimately display the ransom message. However, here we can see a more personalized type of attack
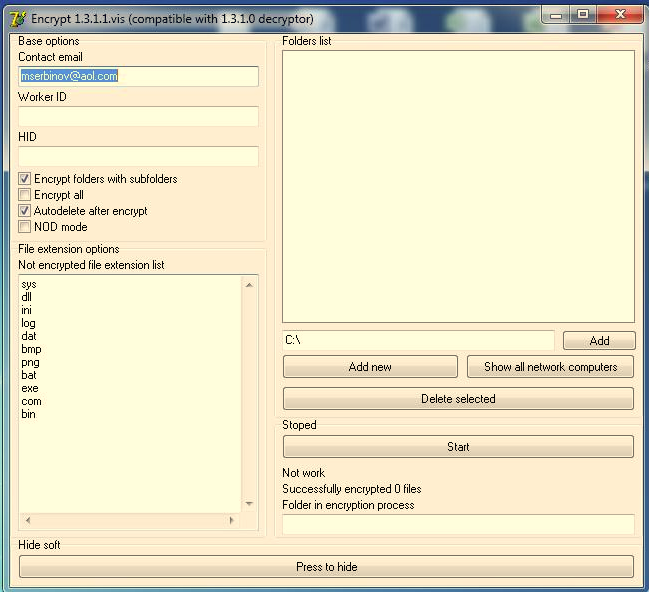
In the intrusion analyzed, we see that the ransomware has an interface through which it can be configured according to the attacker’s preferences, starting with the email address that will appear in the ransom note that will be sent to the victim.
With this customized attack, it’s possible to hand-pick the network computers whose information the attacker would like to encrypt, choose files, self-delete upon completing the encryption, enter stealth mode, etc.
How to protect your business from customized attacks
The survival of any company in a digital environment calls for establishing a solid corporate network security strategy. Prevention in the face of unknown cybersecurity threats with the goal of neutralizing it as soon as possible, or blocking an attacker should he succeed in gaining entry to the system, plays a role of top priority today.
In the present case study, from PandaLabs we blocked attack attempts that used this form of ransomware against companies protected by Adaptive Defense in Germany, Belgium, Sweden, and Spain.
Here are the MD5s of the ransomware:
4C163E182FFBA6C87EA816B7D7A7D32B
D9489263DA3A5CA7E938315EFD32522D
A timely investment in prevention, detection, and response technologies, instead of adopting perimeter-based solutions, guarantees better preparation in the defense against cyberattacks.




4 comments