Scroll to the bottom for the latest updates…
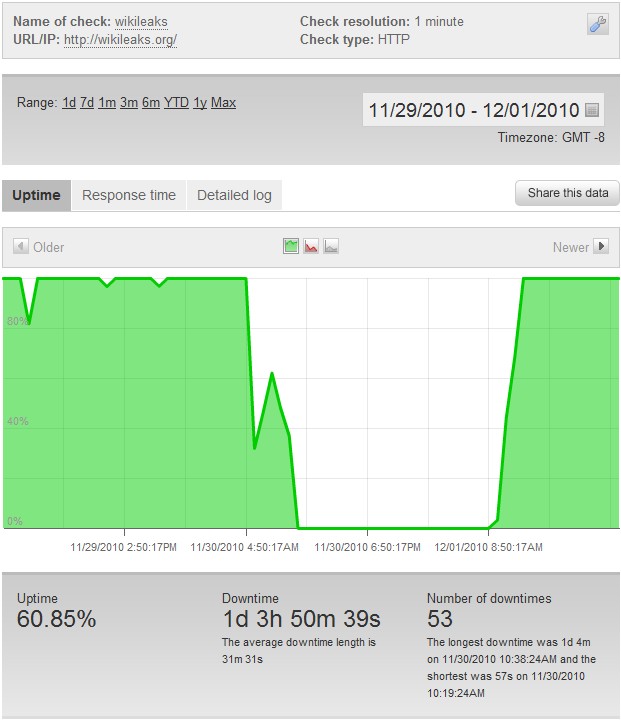
DDoS attacks are flying across the Internet like there is no tomorrow. Just a few days ago, a hacktivist operating under the handle “th3j35t3r” decided to single-handedly take down the Wikileaks website with a DoS tool of his (or their) own creation. He issued a statement on Twitter shortly after explaining that the attacks against the WikiLeaks website were made for “attempting to endanger the lives of our troops, ‘other assets’ & foreign relations.” According to our statistics, his attacks resulted in 1 day 3 hours and 50 minutes of downtime for WikiLeaks before the site was completely yanked offline by Amazon and EveryDNS.
Note: Initiating a DDoS attack is illegal in many countries and we do not recommend that you participate in this or future campaigns.
On the other side of the attack spectrum, the anonymous attackers involved in Operation:Payback have vowed to take a temporary break from their mega-assault on the entertainment industry in order to spend some time helping WikiLeaks. Their first attack has been set on PayPal, after the U.S. based company closed its doors on WikiLeaks citing an AUP violoation.
PayPal issued the following statement on their blog:
“PayPal has permanently restricted the account used by WikiLeaksdue to a violation of the PayPal Acceptable Use Policy, which states that our payment service cannot be used for any activities that encourage, promote, facilitate or instruct others to engage in illegal activity”
Shortly after the PayPal announcement, Anonymous decided that the PayPal Blog would be its first DDoS target in Wikileaks related counterattacks.
The following statements were released on an Anonymous Twitter account:
“TANGO DOWN — thepaypalblog.com — Blog of Paypal, company that has restricted Wikileaks’ access to funding. #Paypal #Wikileaks #WL #DDoS”
“Close your #Paypal accounts in light of the blatant misuse of power to partially disable #Wikileaks funding. Join in the #DDoS if you’d like”
According to our stats, ThePayPalBlog.com has been down as of 4AM PST on 12/4/2010 and shows no sign of coming back online anytime soon.
Anonymous organizers had this to say in regards to the temporary switch in focus,
“While we don’t have much of an affiliation with WikiLeaks, we fight for the same: we want transparency (in our case in copyright) and we counter censorship. The attempts to silence WikiLeaks are long strides closer to a world where we can not say what we think and not express how we feel. We can not let this happen, that is why we will find out who is attacking WikiLeaks and with that find out who tries to control our world. What we are going to do when we found them? Except for the usual DDoSing, word will be spread that whoever tries to silence or discourage WikiLeaks, favors world domination rather than freedom and democracy.”
Update – 12/4/2010 – 10:50 AM PST:
After nearly 7 hours of constant attacks, the PayPal blog has either been deleted or permanently taken offline. Accessing the blog this morning revealed the following 403/access forbidden error:
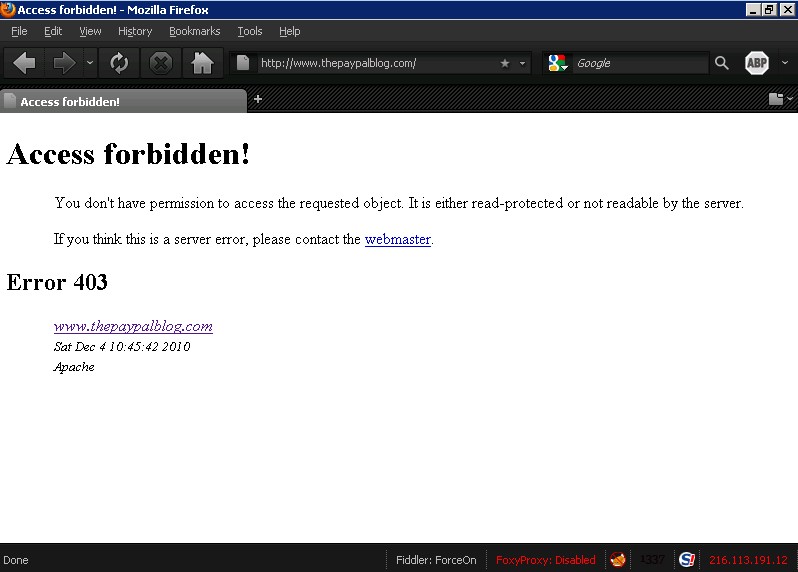
Update – 12/4/2010 – 1:24 PM PST:
ThePayPalBlog.com is no longer resolving to the 403 error page and is completely down again.
Update – 12/4/2010 – 2:50 PM PST:
PayPal has reduced its entire blog to a plain text statement regarding their decision to suspend WikiLeaks.
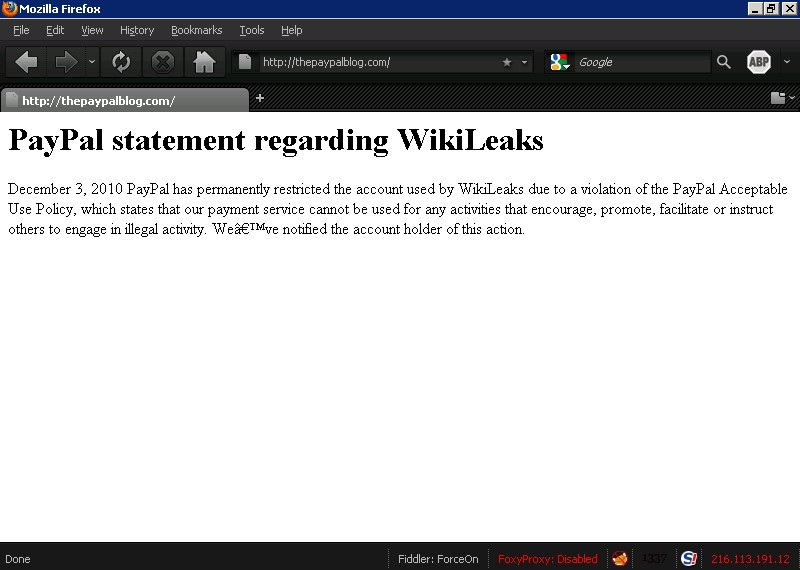
Update – 12/5/2010 – 1:28 PM PST:
ThePayPalBlog.com is now back up after 75 service interruptions and 8 hours 15 minutes of total downtime. This report doesn’t take into account the many hours that ThePayPalBlog.com resolved to a 403 error.
Update – 12/6/2010 – 3:06 AM PST
Official plans to support WikiLeaks have been announced.
Update – 12/6/2010 – 12:00 PM PST
Anonymous has launched its second attack on the main PayPal website. Minutes after they announced the launch of the attack, their infrastructure started to take a hit. Their website is now unavailable and presumably under counter DDoS attack.
The following poster has been circulating on the Internet:
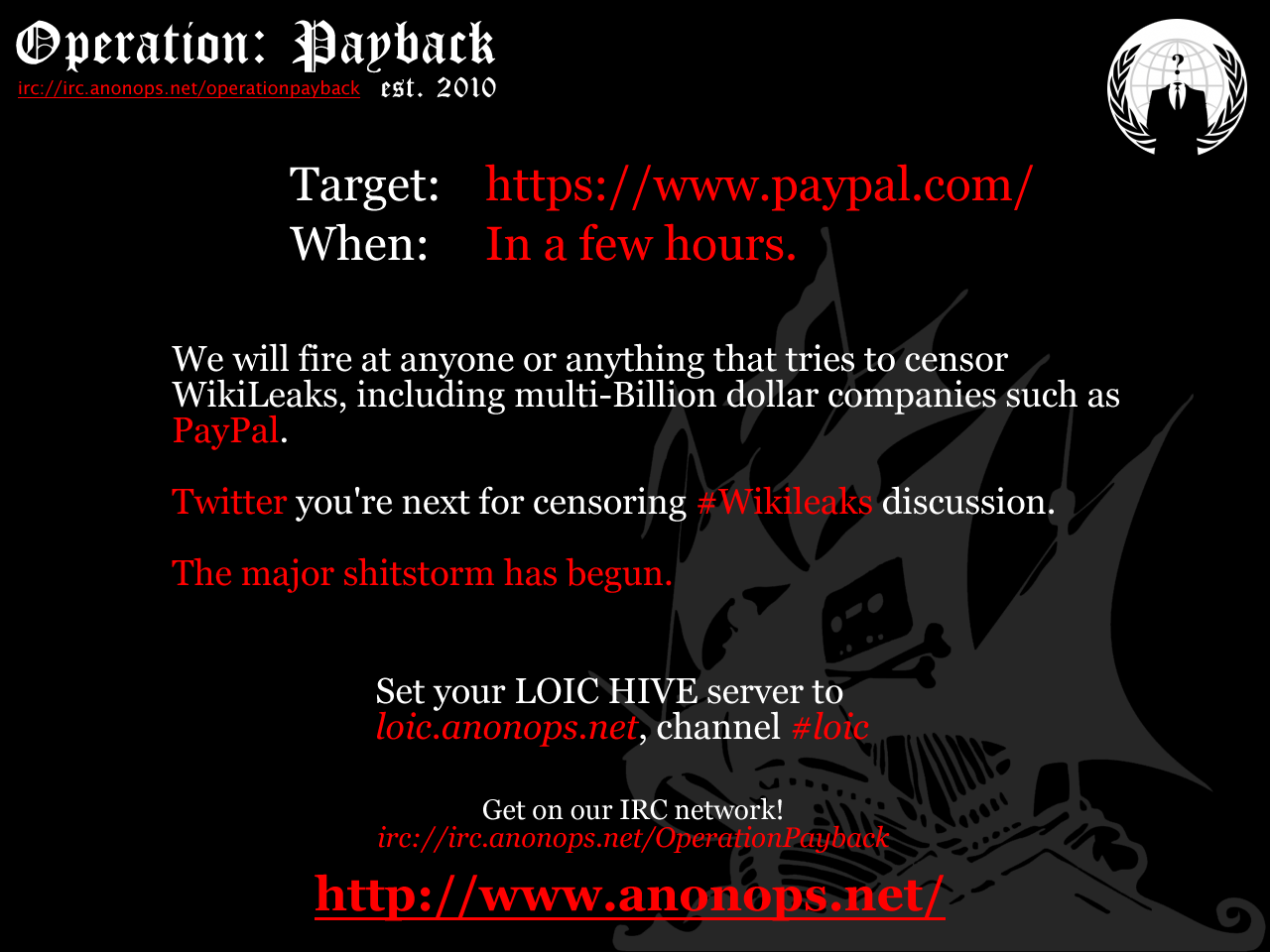
Update – 12/6/2010 – 12:30 PM
They are now going after postfinance.ch, the bank that took down Julian Assange’s defense
fund. We have recorded 5 minutes of downtime so far.
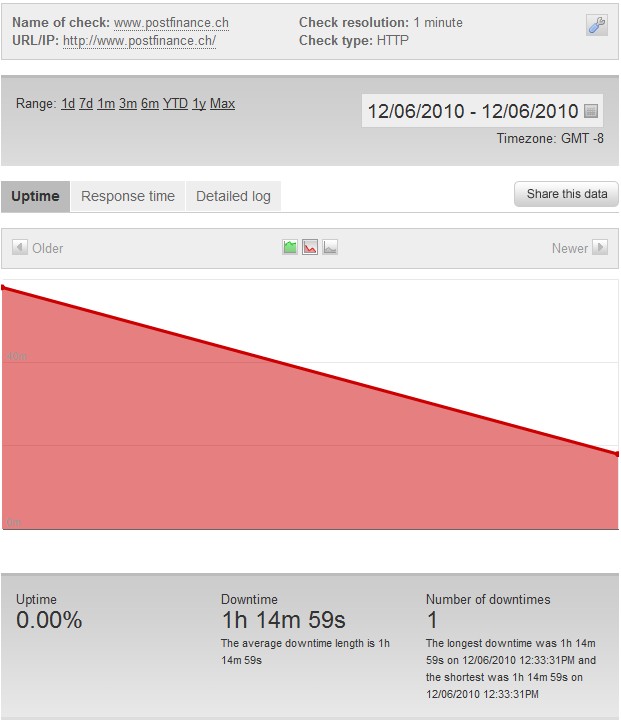
Update – 12/6/2010 – 1:52 PM
The attack on postfinance.ch is ongoing. The site first went down at 12:33 PM PST and has been down for over one hour.
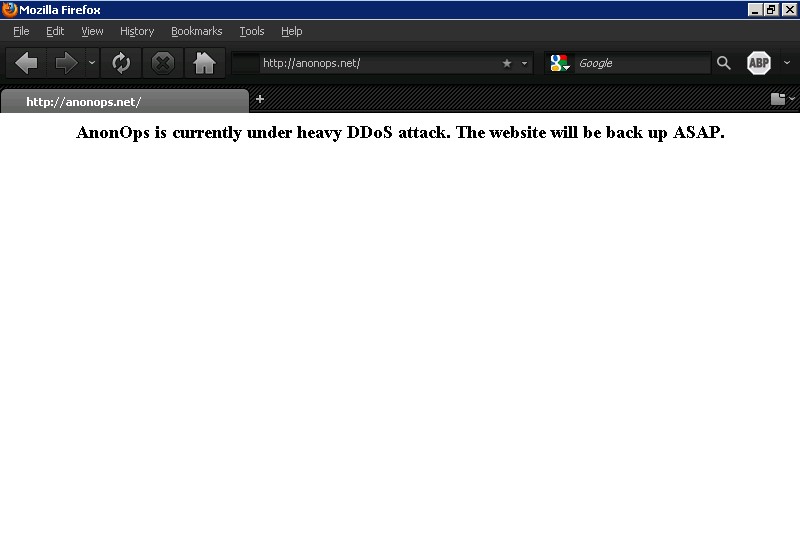
Update – 12/6/2010 – 3:02 PM
The Anonymous website is currently under heavy DDoS attack. We’ve observed just under 2 hours of downtime and 23 service interruptions since the pro-wikileaks attacks started this morning.
Update – 12/6/2010 – 5:07 PM
The attack against PostFinance.ch is still underway. We have observed 4 hours 41 minutes of continuous downtime since the attack started.
In addition to the DDoS attack, some Anonymous members are spamming PostFinance offices with the following image.
Update – 12/7/2010 – 12:03 AM
The attack against PostFinance.ch is still going strong with 11 hours 35 minutes of recorded downtime and counting.
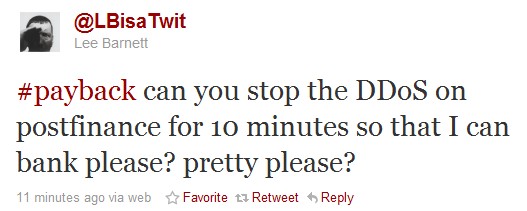
This DDoS is one of the first successful attacks on a financial institution and is getting in the way of customers doing business with the company. One user wrote on Twitter, ” #payback can you stop the DDoS on postfinance for 10 minutes so that I can bank please? pretty please?”
Update – 12/7/2010 – 9:30 AM
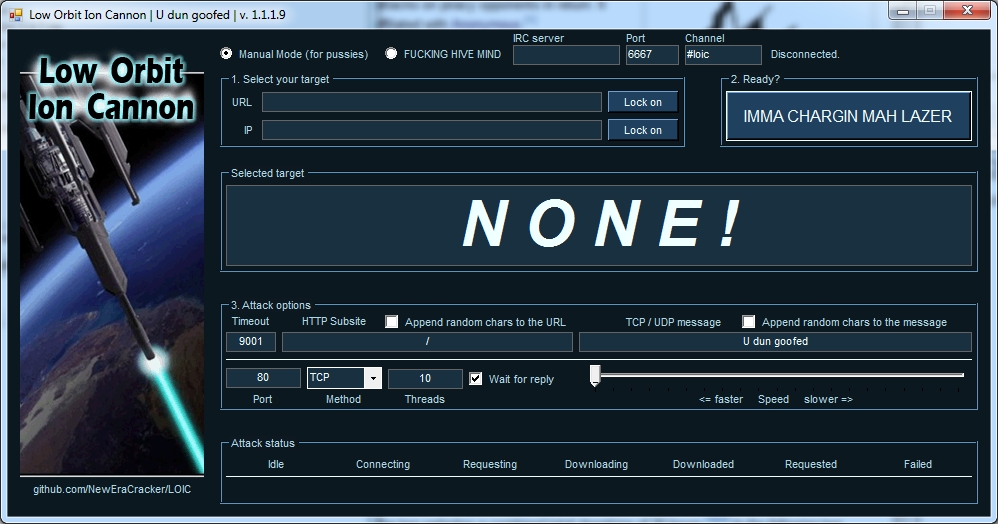
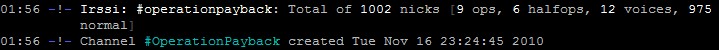
Anonymous attacked postfinance.ch well into last night, with 16 hours and 30 minutes of recorded downtime. The chat room currently has over 900 people joining in on the attack, as well as over 500 computers involved in their voluntary DDoS botnet (LOIC HIVEMIND).
(Low Orbit Ion Canon) is a DDoS tool developed by the attackers to carry out their DDoS attacks. The software allows users to insert a command and control address into the application, which will then automatically connect their computer to the “HIVEMIND” and immediately start attacking a predetermined target.
Here is what the software looks like:
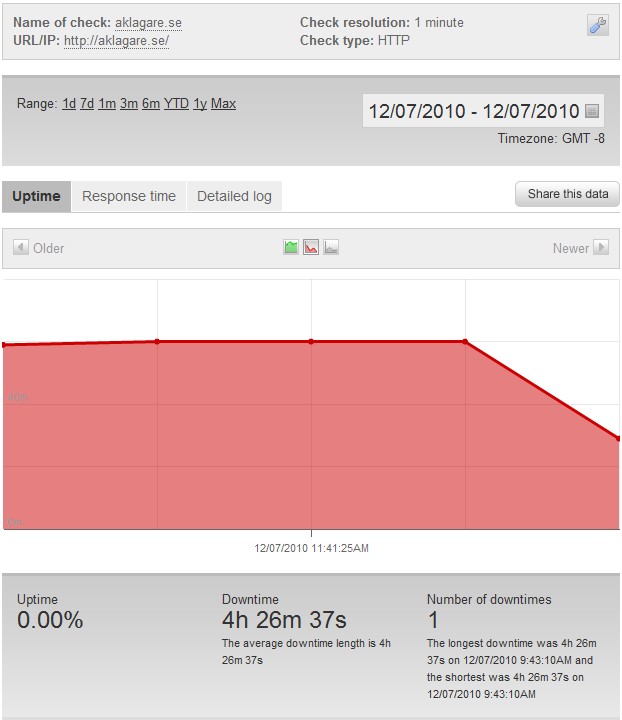
Update – 12/7/2010 – 9:44 AM
The target has switched over to http://aklagare.se, the Swedish prosecutors. The website was down instantaneously after the target was selected with over 500 computers in the voluntary botnet attacking the site all at once.
Update – 12/7/2010 – 10:16 AM
Over 1000 people have joined the chat to participate in the attacks against anything anti-WikiLeaks.
Update – 12/7/2010 – 2:10 PM
We have recorded 4 hours 26 minutes of downtime for Aklagare.se, since the attack started focusing on the site at 9:44AM PST
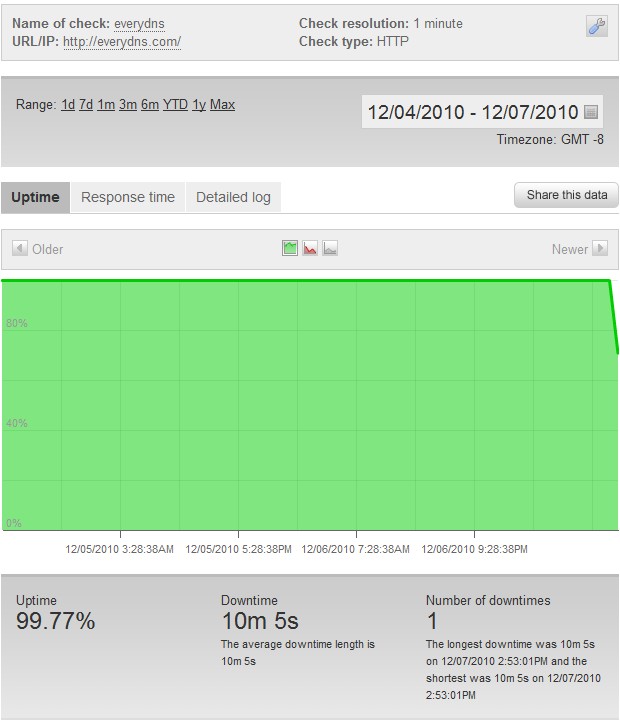
Update – 12/7/2010 – 3:06 PM
The target has been switched to EveryDNS.com, the DNS provider that took WikiLeaks down. The target was announced at 2:52 PM PST and the website was taken down just one minute later at 2:53 PM PST. We have 10 minutes of recorded downtime and counting:
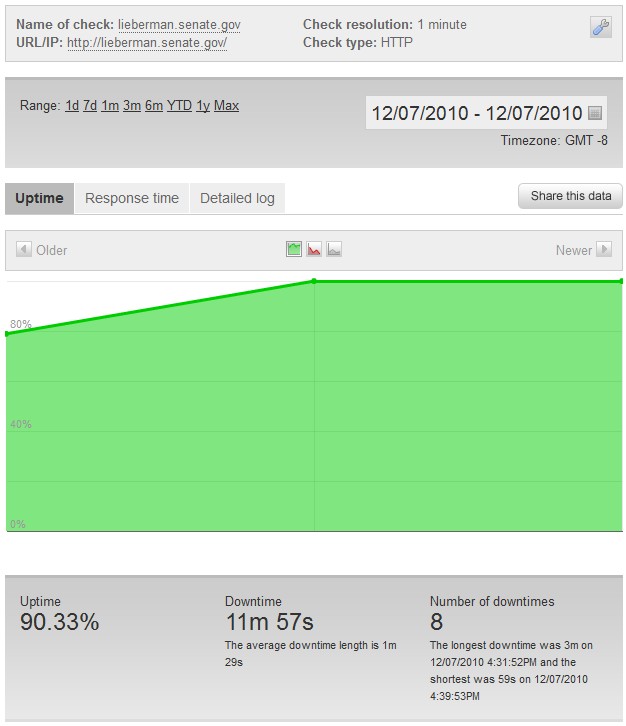
Update – 12/7/2010 – 3:51 PM
The target has now been changed to http://lieberman.senate.gov. This marks the first time Operation Payback has targeted a government site under “Operation Avenge Assange.”
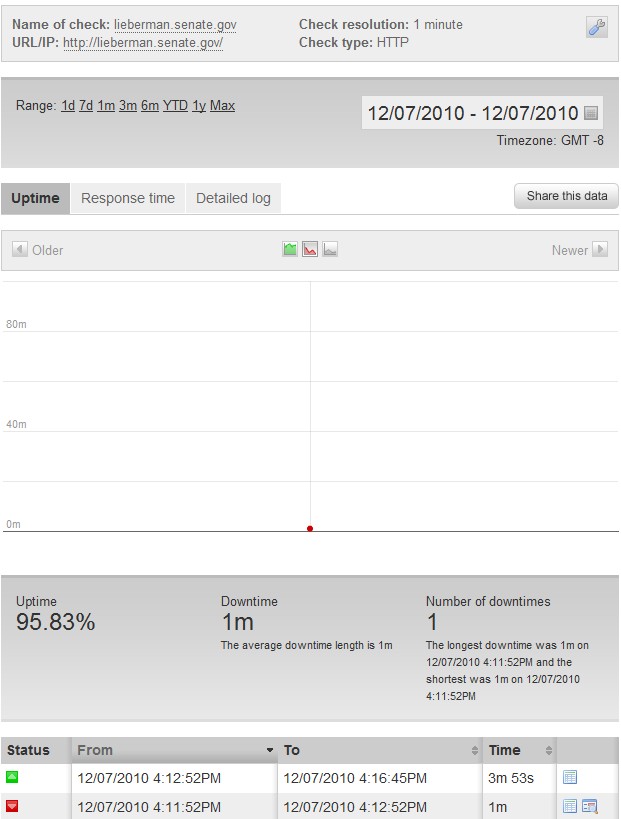
Update – 12/7/2010 – 4:16 PM
We have recorded the first downtime for lieberman.senate.gov. There are currently just under 1,000 attackers in the chat room and almost 600 computers connected to the voluntary botnet.
http://lieberman.senate.gov went down for 1 minute at 4:11 PM PST:
Update – 12/7/2010 – 4:56 PM
has been under a constant DDoS counter-attack, but the attacks against the site intensified shortly after announcing the attack on Senator Lieberman’s website. We’re not sure who exactly is involved in the retaliation against the group, but we suspect that it may be a group of patriots attempting to protect the greater interests of the United States of America.
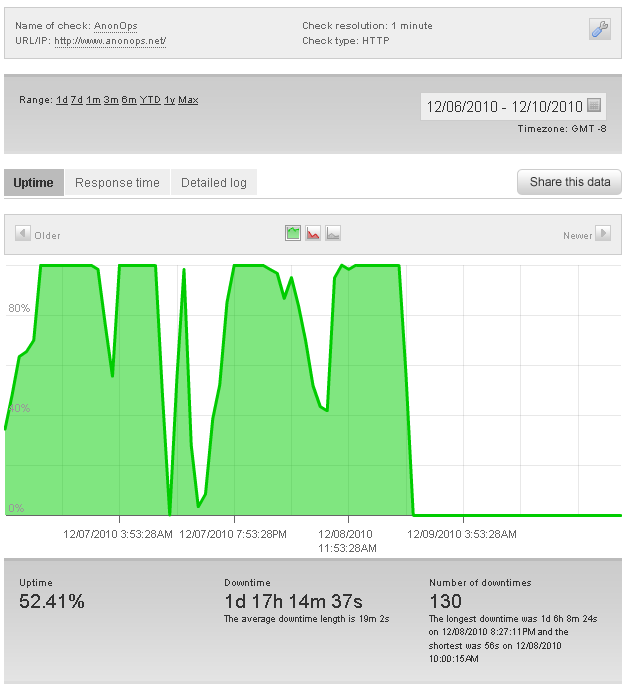
Here is a uptime graph of Operation:Payback’s website:
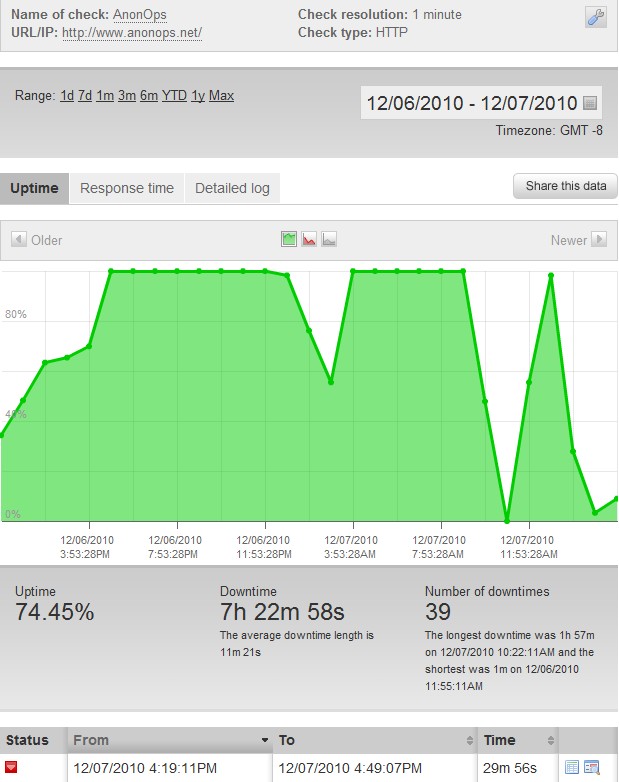
Update – 12/7/2010 – 5:54 PM
The attack on lieberman.senante.gov ended with 8 service interruptions and 12 minutes of downtime. The attack is now back on e-finance.postfinace.ch, which has been hit the hardest with 61 service interruptions and 1 day 2hours 36 minutes of downtime.
Update – 12/7/2010 – 7:20 PM
They have switched targets to www.advbyra.se, the lawyer of the 2 girls who were allegedly raped and/or assaulted by Julian Assange.
The site took only 1 minute to bring down and has been down for the past 15 minutes.
Update – 12/7/2010 – 8:15 PM
A small group of Anonymous protesters (not everyone) have started attacking Sarah Palin’s website (sarahpac.com) in retaliation for stating that Assange should be hunted like a terrorist. We have observed 6 minutes of downtime so far.
![]()
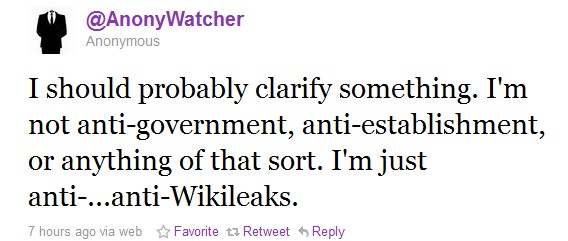
This highlights the fact that no one is “in charge” of this attack campaign. These attackers make target suggestions and follow along at will… even if just a few of them are on board with it.
Update – 12/8/2010 – 1:56 AM
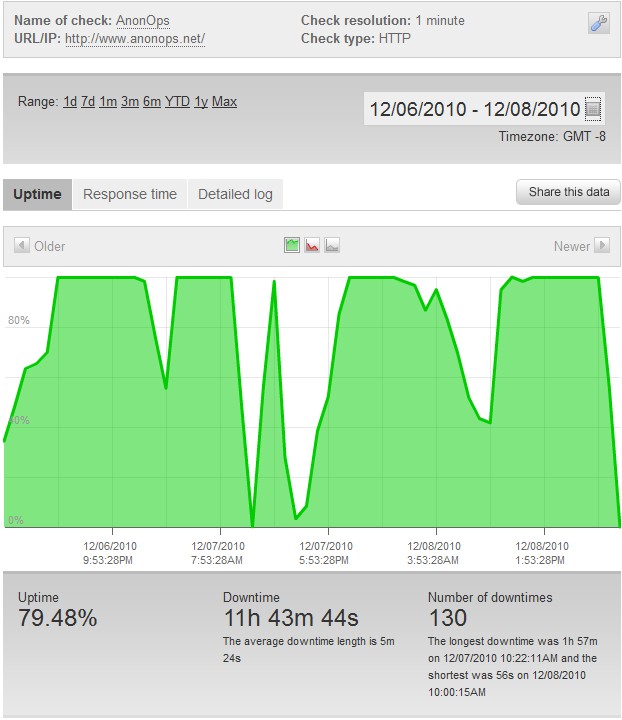
We have observed 256 service interruptions and 94 hours of combined downtime since these attacks started on December 4th. We also observed over 8 hours of counter-ddos downtime on the attackers (anonops.net) site.
Below you will find our latest updated downtime tracker:
Note: Each site name can be clicked on and will take you to the corresponding part of the blog post.
| Site | Interruptions | Downtime (h:m) |
| ThePayPalBlog.com | 77 | 8:19 |
| PostFinance.ch | 55 | 33:08 |
| e-finance.postfinace.ch | 61 | 33:07 |
| www.aklagare.se | 11 | 13:00 |
| everydns.com | 4 | 0:31 |
| lieberman.senate.gov | 8 | 0:12 |
| ADVBYRA.SE | 32 | 5:11 |
| sarahpac.com | 8 | 0:25 |
| TOTAL | 256 | 94 hours |
Update – 12/8/2010 – 2:37 AM
This attack campaign evolves so quickly that they already started targeting MasterCard.com while I wrote my last update for the night.

MasterCard.com first went down at 1:14 AM PST with 4 service interruptions and is currently experiencing 1 hour+ of ongoing downtime.
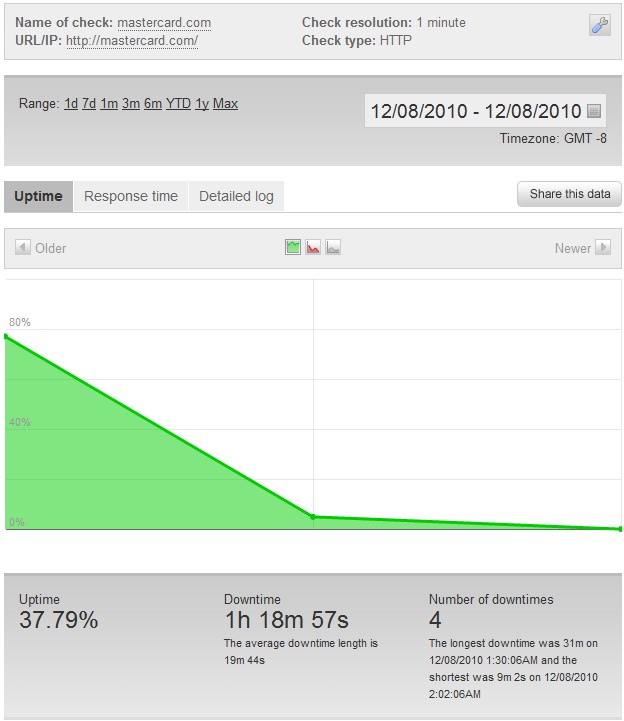
Update – 12/8/2010 – 3:17 AM
The Internet hosting provider (space2u.com) of the Lawyer representing the 2 girls who were allegedly raped/assaulted by Julian Assange has voluntarily suspended the ADVBYRA.SE website indefinitely.
Here is a snip of the conversation taken from the chat:
This marks the first time a website has been voluntarily removed by an ISP as a direct result of “Operation Avenge Assange.”
Update – 12/8/2010 – 5:18 AM
Mastercard.com is still down with 940 computers in the voluntary botnet attacking the site all at once. We have 3 hours 57 minutes of recorded downtime so far.
Update – 12/8/2010 – 8:24 AM
Mastercard.com is still selected as the main target and has not came back online since our last report. 7 hours of downtime and counting.
The amount of participants in the attackers chat room have soared to over 2200 people and there are currently over 1,700 computers in the voluntary botnet.
Update – 12/8/2010 – 12:26 PM
Mastercard.com still under attack with 11 hours of downtime and counting, but the target will change to Visa.com at 1 PM PST.
This is the first time that the group officially targets Visa.com, but we have already observed 106 service interruptions and over 12 hours of downtime for Visa since we started monitoring yesterday at 9PM.
Update 12/8/2010 – 4:14 PM
Twitter has suspended the @anon_operation account.
Update – 12/8/2010 – 8:11 PM PST
Operation Payback has selected PayPal as a target again. We have observed PayPal’s very first downtime at 6:43 AM today and the site has been going up and down ever since.
We have observed 33 minutes of total downtime and response times in the 2,600-4,000 ms region.
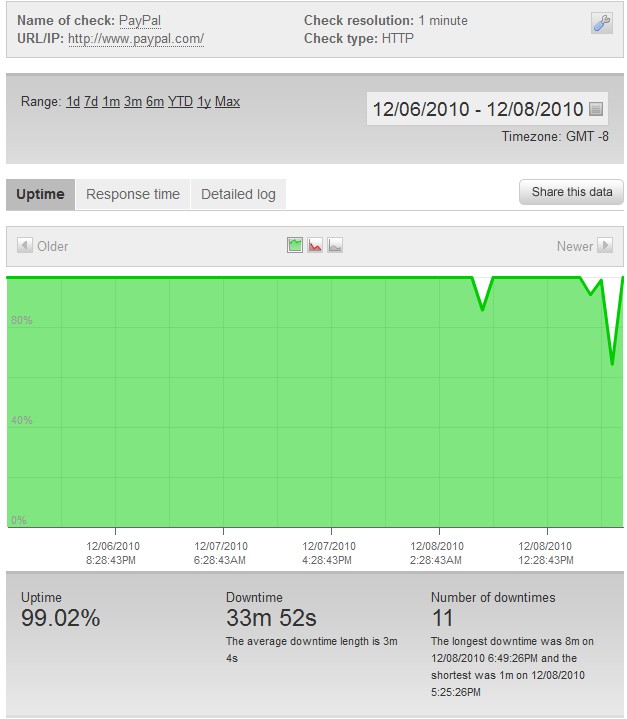
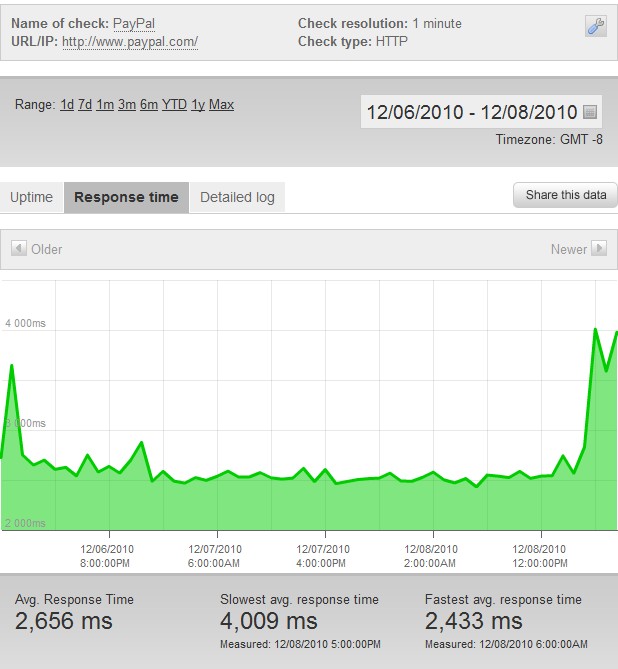
Update – 12/8/2010 – 9:00 PM
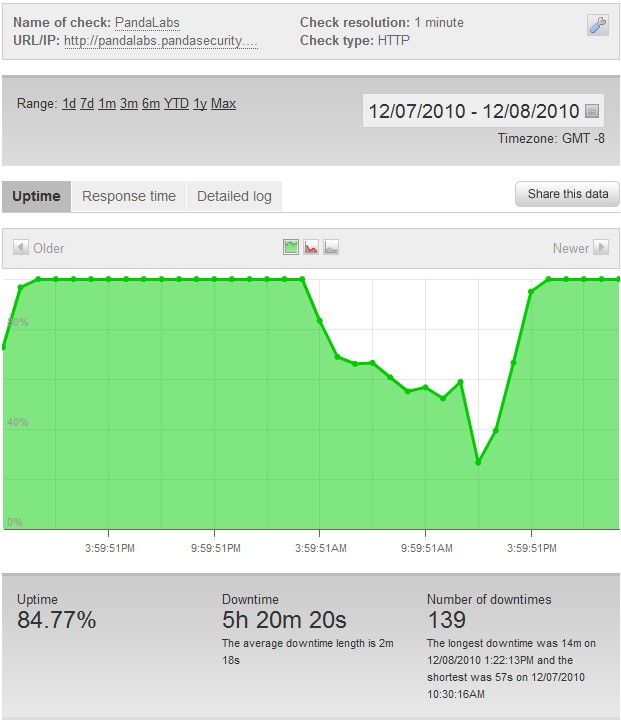
If you have been following our blog post today, then you may know that we were under a constant and steady DDoS attack throughout the day. In the spirit of this post, I’ll go ahead and announce that the PandaLabs blog sustained 139 service interruptions and over 5 hours of downtime today. It’s still unclear as to who exactly is to blame for the attack, but it’s obvious that they did not want these attacks documented for the general public.
People have been asking me all day if there is some sort of “patriot response” to Operation Payback and there is no doubt in my mind that an initiative does exist, but no one besides @Th3J35t3r has publicly “attacked back” and he/they still haven’t said anything about these latest attacks.
So, what makes me think that there is some sort of underground patriot response? Well, let’s take a look at the statistics….
The Operation Payback website has sustained a series of DDoS attacks despite being hosted on a “bulletproof” server specializing in anti-ddos and hosted in Russia.
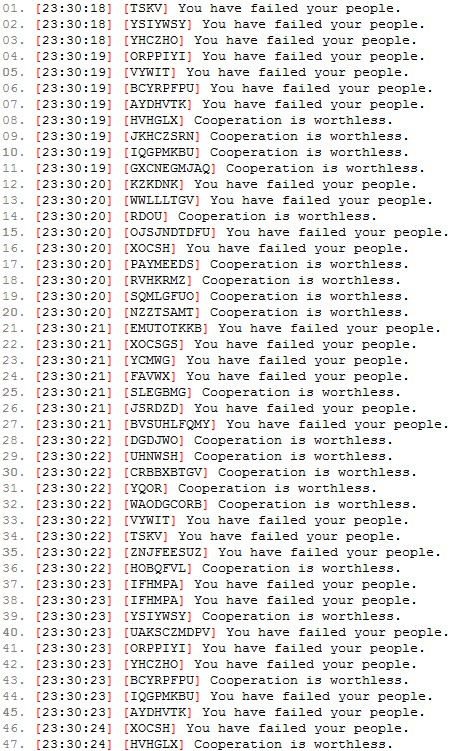
The Anonymous chats server has periodically become flooded with bots. Here is some of what they had to say:
PandaLabs Blog Downtime:
I expect more counter-attacks as Operation Payback progresses, but it’s still unclear if these patriots will ever make themselves publicly known.
Update – 12/9/2010 – 1:13 AM
There are currently over 500 computers in the voluntary botnet (LOIC Hivemind). They are all targeting paypal.com (note: not www.paypal.com), which has been unresponsive for the past 1 hour 20 minutes and counting.
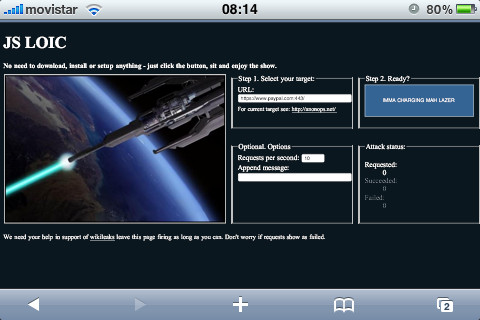
Update: 12/9/2010 – 11:15PM – Luis Corrons:
A JS version of LOIC is available for the participants of the attack, only a browser is needed, so you can even launch the attack from an iPhone.
Update: 12/10/2010 – 2:20AM – Luis Corrons:
Attacks are going on in all directions. While the next step was to attack amazon.com, Anonymous’ server infrastructure was heavily attacked, and in fact they have been taken offline for a long period of time during the day. Right now they are currently regrouping and strategizing for future attacks.
Here is an uptime graph of Operation:Payback’s website:
Update 12/10/2010 – 12:00 PM PST
There have been reports of a new Anonymous initiative called “Operation:Leakspin,” which is aimed at reviewing and exposing sensitive confidential information taken from the WikiLeaks releases.
Here is the announcement image:
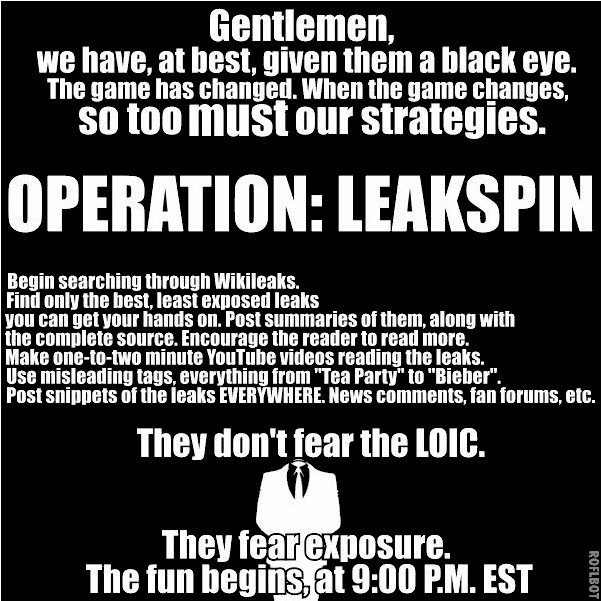
In speaking to Operation:Payback organizers, they have maintained that they have nothing to do with this new initiative. This highlights the fact that a group like “Anonymous” has no leaders and therefore cannot be easily controlled. Members split up and form their own initiatives when they want or feel the need to. In this case, we suspect that this new initiative came to light after Operation:Payback communication infrastructure was crippled most of yesterday and today. It’s still unclear as to what the strategic direction of the Operation:Payback will be in the future, but it looks like the original group is starting to split up into several splinter operations.
Update: 12/11/2010 – 12:10 PM
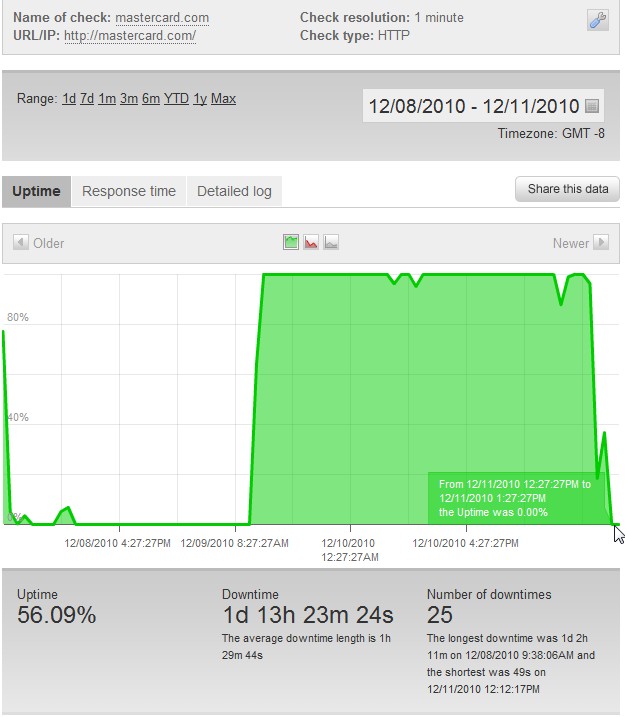
Operation:Payback is back after suffering from infrastructure issues, which caused their IRC network to be unavailable for quite some time. The chat room is currently filled with over 1,200 users, many of which are targeting mastercard.com.
Mastercard.com started to slow down at around 6:43 AM PST this morning and went down completely at 12:27 PM PST. We have recorded a total of 1 day 13 hours and 23 minutes of downtime for mastercard.com since the attacks started on December 8th.
Update – 12/11/2010 – 2:03 PM
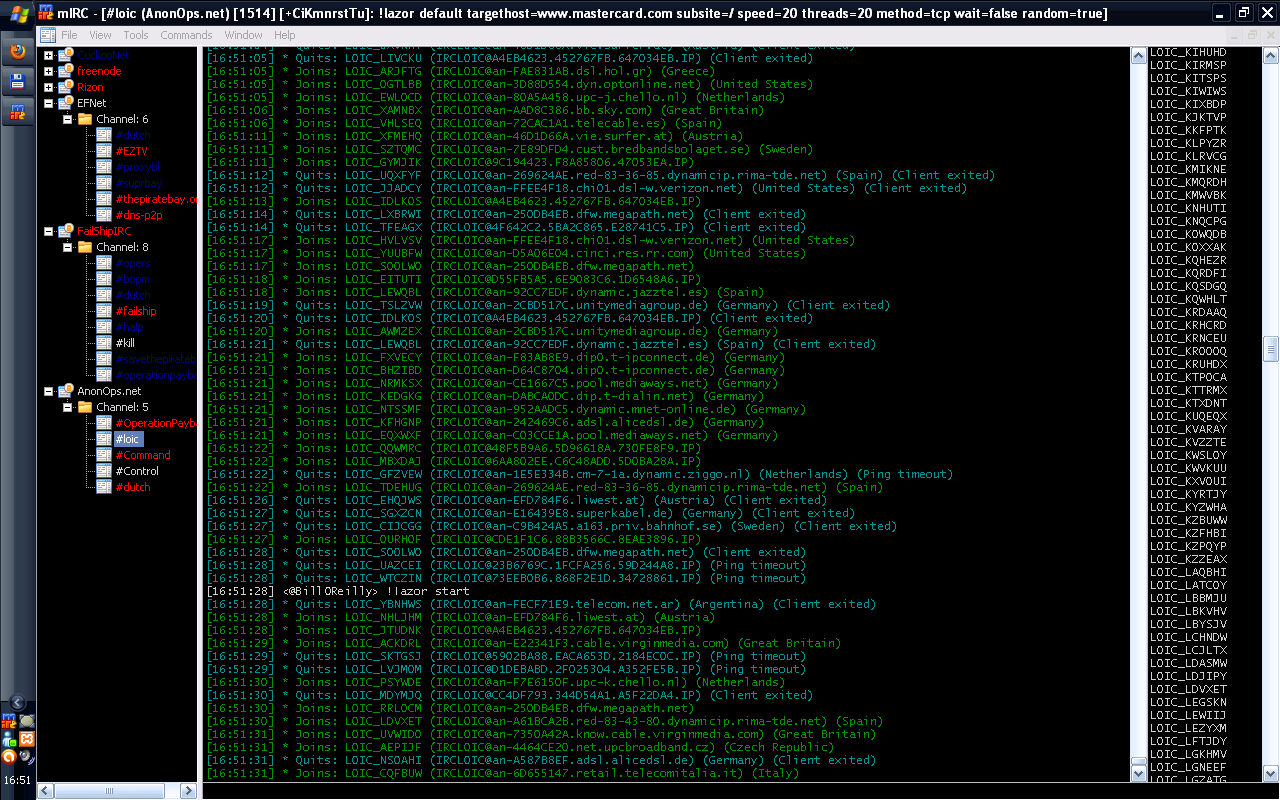
Many people have asked us how the anonymous voluntary botnet (LOIC hivemind) works. After the LOIC DDoS tool is installed and running on a computer, the user must first insert the command and control (IRC) server into the program. Once the C&C is set, the software will then automatically connect the computer to the #loic IRC control chat room under the user name LOIC_+6 random alphanumeric characters.
The person in control of the #loic chat room (in this case @BillOReilly) will then set the topic to initiate the coordinated attack on all of the volunteer computers. Here is what a typical command looks like:
!lazor default targethost=targetdomain.com subsite=/ speed=20 threads=20 method=tcp wait=false random=true
Here is a screenshot of what the room looks like:
Note: Initiating DDoS attacks is illegal in many places in the world. We do not recommend that anyone participates in these attacks!
Update – 12/13/2010 – 2:31 AM – Luis Corrons
A second person has been arrested in the Netherlands for having joined the DDoS attacks coordinated by Anonymous. In some countries, such us the Netherlands or UK, participating in these kind of attacks is considered a crime, while in others there is no yet legislation on this topic.
It is important to note that the LOIC (Low Orbit Ion Canon) tool provided by Anonymous doesn’t mask the IP address of the user, so anyone using this will be sending his IP address with the attack.
Update – 12/13/2010 – 8:30AM PST – Sean-Paul Correll
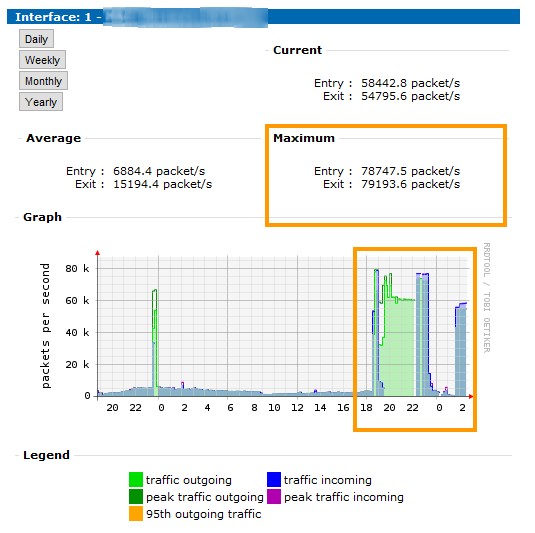
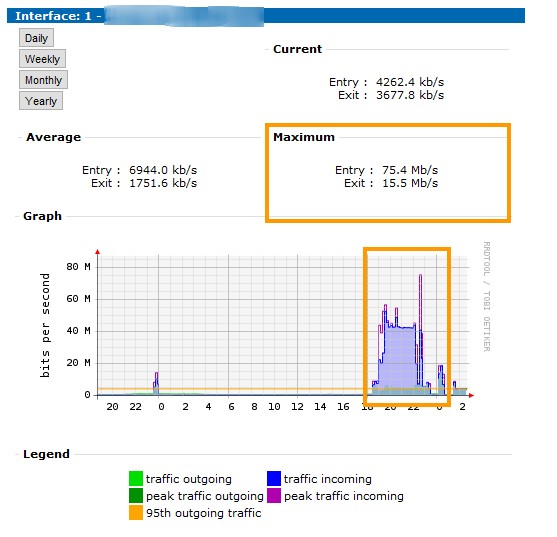
There have been wide scale attempts at shutting Operation:Payback down. One server operator going by the handle MoztoX told us that one of his servers was DDoS’d well into late last night. “We’re receiving 130kb packets coming in at a rate of 80MBit/s,” he said. Another Operation Payback organizer said that the attacks were, “fairly powerful,” but that “nothing is ever cancelled / OP will be here until we are no longer needed / our stated mission and goals remain.” When asked where he thought the attacks were coming from, he simply stated, “unsure at the moment,” “…the obvious assumption would be twofold / companies that have been targeted by the users of our irc is one / 2 would be anyone else out there who disagrees with our views”
The graphs MoztoX provided (below) show a sudden 1000% increase in traffic:
Twitter and Facebook have also made attempts at silencing the group by suspending organizer profiles, which lead from having just a few “official” profiles to a ton of unconfirmed profiles. The situation has escalated to the point where several groups are releasing statements out to the media without the knowledge of the original Operation:Payback organizers. In addition, the publication of the arrests taking place in the Netherlands has lead to a steady stream of incoming Dutch supporters. They even have their own chat room inside of the network.
From our view, this sudden increase of supporters mixed with takedown efforts are creating a splintering effect, where the original organizers are tasked with focusing on reacquiring infrastructural assets instead of strategic direction of the group. A great example of this was the Operation:Leakspin initiative, which came to light after the group sustained one of its first hard hitting DDoS attacks. These destabilization efforts have left many supporters unclear as to what the direction of the group is and we started observing smaller coordination efforts all with slightly different missions from what the organizers originally intended for Operation:Payback. One example of this is the Operation:Daylight initiative, which was created by a former Operation:Payback organizer.
These changes are going to make reporting and confirmations extremely difficult because there is no longer a central source of communication with the organizers. This is not one massively coordinated campaign anymore, it’s pure anarchy.
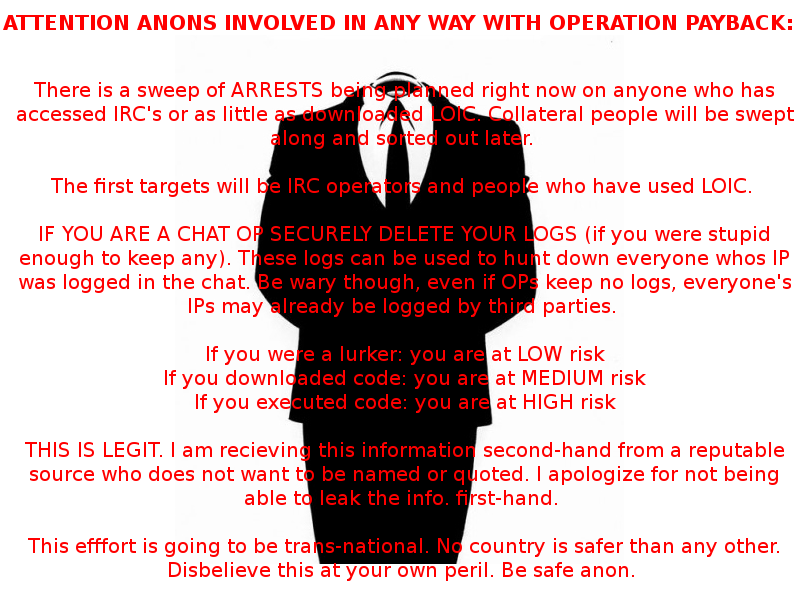
Update – 12/13/10 – 11:00 PM PST – Sean-Paul Correll
The following image urging Anonymous members involved with Operation:Payback to “securely delete” all logs and cease all illegal activity immediately has been making its rounds on the Internet.
“Ridiculous, this is an obvious ploy to try and scare people away,” said one Operation Payback organizer going by the handle “shitstorm”
The image goes on to state that DDoS supporters are at low risk if they were just observers (lurker), medium risk if they downloaded the DDoS tools, and at high risk if they used the DDoS tools. The organizers that I spoke to do not agree with the message in this image and even went on to bash the spelling errors in the image. “It’s a troll,” stated another organizer who wished to continue to remain Anonymous.
I should point out (as we have before) that the voluntary botnet connections are not encrypted or obfuscated in any way. IP information is transmitted to whichever site the group is attacking, so it’s entirely possible to be traced back.
Another cause for supporter concern is that the organizers could have accepted a server donation (leaf node) from an untrusted source, which could mean that the administrator of this node would have access and logs to all of the information across the entire network. The organizers stated that they don’t think this has happened and that they have a vetting process for new server applicants, although they would not disclose their qualification methods with us.
Update – 12/14/10 – 12:43 AM PST – Luis Corrons
A small group within Anonymous has started the Operation Payback, Mission: Leakflood
It is the first FaxDDoS I have ever seen. This is the “official” announcement:
Update – 12/14/10 – 4:23 AM PST – Luis Corrons
As a self-defined anarchic group, Anonymous has many different things going on at the same time. This particular one has attracted my attention, as it means to take the protest from the Internet to the real life. Called “Operation Paper Storm”, the idea is to have the streets plastered with propaganda the next Saturday December 1.
Update 12/14/2010 – 11:38 AM – Sean-Paul Correll
According to organizers, Google was also among the companies silencing the group. Operation Payback organizers used Google docs to store campaign fliers, as well as conduct polls to determine future targets. It’s unclear as to which part(s) of the Google TOS have been violated by the group, but according to the organizers, several of these polls have been taken offline by the company.
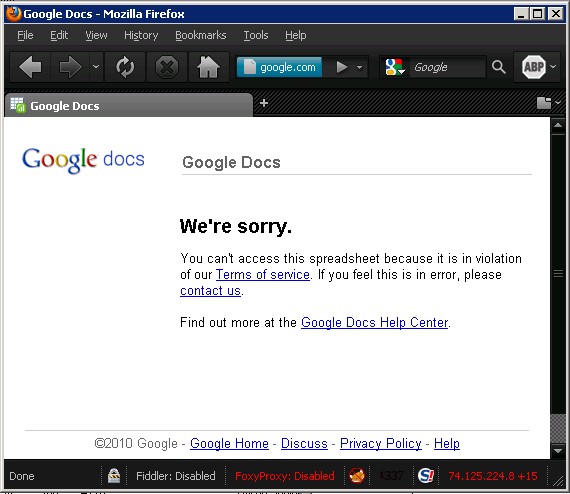
Update – 12/15/2010 – 3:52 PM
There is a small splinter group (20-30) who are attacking a Venezuelan government website. Their reason behind the attacks? President Chavez wants to take steps to censor the Internet in Venezuela.
Operation Payback organizers said that they do not have anything to do with these attacks, but that they could not stop people from doing them. “We don’t support them, but hey, it’s a free world,” said an organizer.
It’s unclear as to what the present direction of Operation Payback is, as no official target has been selected for quite some time. For now it seems that Operation Payback organizers are satisfied with what they’ve done so far. “We have accomplished more than I ever thought possible,” said one organizer.
As for the group of individuals targeting Venezuelan government sites, the site has been down ever since we started monitoring it with over 1 hour of total downtime.
The organizers of that group have also said that they have more Venezuelan targets in mind for the near future.
Check back frequently for updates.








158 comments
Where is the damn #IRC channel so I can join the ddos attack on paypal?
Which server, wich channel?
irc.anonops.net
#operationpayback
irc.anonops.net #operationpayback
Just downlaod “irc-loic”
put “loic.anonops.net” in irc server and click on “hive”.
Its not Censorship, Wikileaks is clearly in violation of the APU of Paypal. Its just an example of how stupid the internet is
You’re an example of not knowing anything about what’s going on…if you knew, and were somewhat intelligent, you might put it together.
irc.anonops.net/operationpayback
Go Go Go!!!!
I think it is time for PayPal and that bank to give Assange back his rights.
Since I have dealt with a PayPal cancelation (as a lawyer), I KNOW that they did not follow their own legal procedures.
anonops.net is under is under DDoS, too
loic.anonops.net
#OperationPayback
@Colum,
Shows what you know about how the law works. Wikileaks has, so far not, not been prosecuted or charged with a crime. Forces of the establishment are investigating the organisation. This does not mean they have engaged in illegal activity and until there is a court verdict that returns a verdict of “guilty” under an alleged charge, Wikileaks, it’s founder, and those working to publish these documents are not guilty of anything.
When pressed, Julia Gillard, Australian PM and lawyer could not name a law under which to charge Assange or treat Wikileaks as a criminal entity. Notable NSW supreme court barristers have published letters to the government in support of the organisation. The American government is attempting to use the espionage act, but there is a long history of precedent they will have to argue against in order for Wikileaks to be guilty of a crime.
Some people shouldn’t throw stones in glass houses…
That user you requested 10 minutes responded: https://twitter.com/#!/LBisaTwit/status/12063181086138368 “#payback thanks, done my banking, can’t believe you listened to me!” LOLOLOL
I just think about 1 thing… Interpol main office is in Lyon (France), if anyone want to organize an anonymous protest in front of it (with our masks, I’m in)
We will be back.
No Infrastructure is secure.
http://www.aklargare.se/ is down^^
This article has been extremely informative. Thank you for the updates.
Very excellent and informative article.
I find Operation Payback a very interesting case of activism.
I must say this Anonymous group is a very intriguing one.
They seem to be almost… unstoppable.
Well, on the internet at least.
We are not an orgnized group. Anonymous is everyone, and no one.
Everyone who operates under the name of Anonymous is working under their own power – we do not have any sort of organization.
I can say that this is the most interesting article that I ever read in this Panda Labs blog currently.
Where do you get the screenshots?
They are currently targeting Mastercard
http://www.mastercard.com is down
Don´t worry! We are from the internet.
Hopefully no judge will codemn us for being abd on the intert. Because that means, we have to be bad IRL.
mastercard.com is down!
They’re back, at least the back-end (europe)
“Dear Customer
The problem at the transaction processor MasterCard is now solved.
We are sorry for the disruption, but we can confirm that all our services are now operational again.
Problem started: 10:17
Problem solved: 16:33
Affected services were:
– Credit Card transactions towards MasterCard”
The current LOIC target seems to be the visa.com website. Interesting to see if they manage to take it down – and quite WHAT will happen when presumably hackers can carry on this for weeks or months if they wish. Frightening but fascinating times.
ISPs are removing sites from their service.. The shitstorm is in full effect.
There is no stopping Anon.
Your MessageI’ve been wondering whether this is the response to the major democracy deficit in Western countries. Governments ignore opinion polls, they ignore sit-ins, they ignore peaceful protests, one doesn’t want to become violent. So maybe financially hurting their precious corporates? It’s not violent, but someone at least pays some price for ignoring the people.
Holy war began!
Thanks for taking revenge for Assange!
Visa.com is down by them…
mastercard.com is up for me
Great updates!
Wikileaks is a valuable asset to humanity and should be respected.
Man hunting Assange will only fuel all of us to seek further truth and accountability from our institutions.
Interesting post!!..
Generally, DDoS attacks are essentially just the Net equivalent of Ring & Run, i.e. pretty juvenile, script kiddie stuff.
But how satisfying has it been to be sitting in class watching while the class clown razzes the teacher into a fluster with his standard tactics, and as much as she would like, she can’t send him to the principal’s office, or rap his knuckles, or threaten to call his parents, because those options are unavailable on the Net.
No, the only retaliatory action open to her is to look back at the kid and go, “Un-uh, YOU neener-neener-neener!”
And she does.
In front of everyone.
Anonymous, you are still the Net’s dorky kid brother, but when we get home I’ll show you where Dad hid all your Dragon Ball DVDs.
Excellent informative article, thank you.
You need to track Paypal.com… it is down. The www subdomain still works though.
They’ve switched from paypal.com to the api, to shut down transactions
http://twitter.com/Billyspub/status/12739317839437824
Thanks a lot for this great summary!
For Great Justice!
The twitter of AnonOps was suspended after having published 10000 stolen mastercard ID.
um wat? At least provide a link to a bogus blog post about stupid vacuous statements like that next time, newfag.
I want IN what IRC?
irc.anonops-irc.com I dunno is it right or not but i got this from:http://portland.indymedia.org/en/2010/12/404283.shtml You better don’t.Your computer will be one of the voluntary botnet.
any stat for api.paypal.com ?
can’t connect to irc everything.anonops.net is not resolving
Hi guys, I suggest a massive authentication trials to the paypal user accounts using random user/pass in order to collapse their database.
Tonight the Dutch Police arrested a 16y boy in ‘Den Haeg’ who was traced down by an special unit of the Dutch police after the attacks on Visa & Mastercard.
http://www.trouw.nl/nieuws/nederland/article3332356.ece/16-jarige_opgepakt_voor__WikiLeaks-aanvallen_.html
(In Dutch so use a translater)
http://anonymouspayback.wordpress.com/2010/12/09/how-to-join-the-anonymous-payback-operation/
hey you panda bears, keep up the good and informative work!
Can we use LOIC to do ddos attack too?if no,why you posted that we can have a try on it?
We do not recommend that anyone participates in these attacks. We do not believe in them and they are illegal in most places.
You refer to a ‘Group of Patriots’, yet a check on their Twitter Feed, and site, reveal they focus their hostility and cyber attacks on Muslim sites. Look, Muslims whether good bad or ugly have nothing to do with Operation Payback or indeed WikiLeaks. Your understanding of Patriot would seem to be somewhat warped…
I believe that they believe they are patriots. I’m sure that many members of Anonymous feel that they are patriots as well.
They consider themselves to be patriots because the sites they attack are Muslim jihadist sites.
The “Muslim” sites that the Jester attacked previously are terrorist recruiting sites that call themselves “Muslim.” They do not represent all Muslims.
Just as the Phelps family calls itself “Christian.”
GPMills, are you claiming that those terrorist recruiting sites previously attacked by the Jester represent all Muslims?
The Jester doesn’t make that claim. Most Muslims don’t accept that claim.
Terrorists who call themselves Muslims are cheering on their new allies from Anon. Terrorists who call themselves Muslims are in possession of the entire unredacted version of the stolen Manning documents. Julian Assange gave them those documents.
I submit GPMills, that you do not have a clue about what you are talking about. Not the slightest clue…
OVER
YOUR
HEAD,
R
Anonymous is fighting for our home. This coat of arms represents that home. Don’t forget whats at stake. http://imgur.com/nhglo.gif
intersting read. keep it up and do it more frequently. people need to be updated.
We’re trying to keep up with everything, but the campaign moves and changes so frequently that it can be hard at times. I’m sure we’ve missed a number of the attacks, but all of the big attacks are here.
Nice work, most comprehensive account of operation payback on the net.anyways mastercard was taken down again yesterday.the newest stage is operation blackface.
Wow, looks like anon got pwnt, i was rooting for them too. Then again from what I have seen anon may get knocked down but they never get knocked out (unless they do it to themselves which is all too common).
moneybookers is dead
also “oficial” statement from op payback twitter
http://dump.no/files/467072ba2a42/ANONOPS_The_Press_Release.pdf
The last attack was on api.paypal.com port 443. Paypal claims there was not disruption but that url is still inaccessible (dec 10) and I know for a fact that some people were not able to purchase from websites using paypal during the attack.
First – I teach PC Classes to at-risk youth (gun toting, drug dealing, car jacking murderers, hookers and gang bangers) in places like Oakland, Hunters Point, East L.A., Harlem and the Bronx (volunteer since 1983) – so I do really appreciate a good rip-roaring game of HackNSack, although as a teacher I can’t play – sorry – the Feds would fry me.
And it is a game – just like Chess – as I teach my kids whether getting a job or building a PC or (ahem) you boys and girls ripping down the HTTPS protection at PayPal, doing man in the middle attacks as explained by HACK5 – YouTube, then grabbing customer data and adding 3 cents to every account to scare the crap out of customers so they all close their credit card and banking accounts – silly things like that – Well, its a game.and you have to make sure what you do is legal – absolutely – and just as important – that you are EFFECTIVE at obtaining your stated objective.
And that is???????? Remember, wild attacks without a clear objective is a waste of your energy and just insane anarchy that hurts everyone – even your mother. Whereas pointed attacks with a clear objective can produce clear results. I think your objectives are to demonstrate to the government that messing with Freedom of the Press in today’s Global Village is going to be painful for politicians and financial entities that support such suppression – is THAT the main objective? A “MESSAGE” to politicians and financial entities?
Or is the objective to GROW AN ARMY of “Fellow Hackers” so you are stronger – and your attacks even more pointed? Is THAT the primary objective?
Or is the objective to “SHUT THE BASTARDS DOWN” (I read that somewhere) – is THAT the primary objective?
Each of these OBJECTIVES has, by their nature, a different GAME PLAN. Right now you are using a little .22 caliber rifle and “plinking” at their armor – not very effective and as some have said – illegal and time consuming and annoying, but not really debilitating. So if you are trying to SEND A MESSAGE, the message the establishment is getting is that you are WEAK ASS PANSIES and I hate when the kids I’ve taught are called that by anyone. I hope your teachers hate it too. PLUS – the message you’re sending to the world is that (ahem) you’re criminals – and that can reduce the size of your Army – although you will pick up some new comers – you alienate yourselves from the rest of the planet.
So – I might suggest that you change your .22 rifle to an 80 MM cannon – by INCREASING the size of your Army and cutting back on the illegal stuff. Is a good ripping DOS attack fun now and then? Perhaps, and certainly I wouldn’t suggest that anyone who thinks its the best method to “send a message” should stop – if that’s the only way you know of to “speak out”. But there are other ways that are legal and can be heard much more loudly and if your goal is to BE EFFECTIVE at obtaining OBJECTIVES – don’t you want to be heard more LOUDLY?
I will remind you what Eric Cantona – French Soccer Player – tried to do – the BANKRUN2010 plan. Well, it failed because not enough people pulled their money out of banks on Dec. 7th. But his heart was in the right place.
Perhaps if you wise guys add this message to EVERY POST – “PULL YOUR MONEY OUT OF EVERY BANK – AND BUY SILVER AND GOLD COINS, USE THEM TO TRADE AND BUY GOODS, AND JUST STOP PAYING ON YOUR CREDIT CARDS” etc. – they’ll get the message – and that’s 100% legal and boy – will THAT be heard at a roaring volume – PLUS – you will profit so much buying silver coins (and necklaces, earrings – whatever) that you can afford to keep up your DOS activities if you should so choose…not that I would support that – I can’t – I only teach kids HOW to hack firmware, dynamic link libraries, BIOS, networks and always – 100% of the time – to – you know – get a job with Intel. I would absolutely never suggest my kids perform a DOS attack on someone like PayPal – one of the biggest unethical, lying, rip-off criminals in the global financial world.
Also – can someone let me know where the damn chat room is – I love hearing my kids rage – channeling that incredible energy into a laser beam is one of the most fun, exciting parts of teaching them to build lasers…for legal purposes…of course.
u mind if i post this to current, under “anonomous advice”, this page is already linked to a story, just thought more people would read it, up to u, email me ye
IRC shouldn’t have been hard to find if you have twitter. Anyway, here’s the current servers:
osiris.anonops.net (196)
`-sobriquet.anonops.net (2)
|-creative.anonops.eu (2)
|-power.anonops.eu (1)
| |-firefly.anonops.eu (14)
| |-anansa.anonops.net (21)
| |-synergy.anonops.net (22)
| `-koldsun.anonops.eu (21)
|-fancy.anonops-irc.com (68)
|-tiny.tritnaha.com (3)
|-vendetta.anonops-irc.com (712)
|-nexus.anonops.eu (256)
|-dragon.anonops-irc.com (188)
|-thealps.anonops-irc.com (22)
|-teamslack.anonops.eu (104)
|-clerk.anonops.eu (1)
|-lexus.anonops.eu (62)
`-nitrox.anonops.net (74)
The State Department should not have pressured Amazon, Paypal, Visa, and Mastercard to turn away WikiLeaks. Aside from the futility of such a move (the cat is now out of the bag), it significantly affects everyday businesses around the world which rely on established ways to get paid. The last thing they need during this holiday season is to be embroiled in politics.
As things stand now, those offended by Paypal might not use it, or its partner ebay. Those offended by Amazon, might not order the kindle. Those offended by Visa and Mastercard might use cash or checks. Worse, they may not buy much for Christmas – – even forego that planed trip, or dinner at that nice new restaurant.
And all for naught.
To be sure, the State Department is recoiling from its decision. Yet, in fear of losing face, it is paralyzed and not likely to change course. It has, however, put away the club, and as such Amazon, Paypal, Visa and Mastercard should quickly reverse course.
The State Department might be the first to be relieved from such open defiance.
For any who may be interested…
http://numrl.com/29391
I am a supporter of Operation: Leakspin but had my fair share of supporting Payback as well. The Anon group is growing at rapid proportions and like any group without a settled figurehead, it gets out of control. Anon is made up of a lot of youngsters as well which does not help the cause. They are easily riled up and want to attack larger and larger sites like interpol and .gov. IRC is flooded with chats about which target to get next. It is also flooded with trolls and definitely people who are working against the Anonymous group and Wikileaks.
We’re trying to move people away from this aggressive behavior because we feel that educating the populace on the actual matter is more important.
Operation: Payback is only another faction, a powerful one, that concentrates on ‘payback’ to large companies who have pushed their weight against Wikileaks. DDoS attacks are effective but largely ineffective against the companies themselves. Anonymous stated earlier today in IRC that there would be a ‘final’ target and to wait for it via twitter.
While Operation: Leakspin is a break off of Anonymous’s original group, it is still an important movement. We believe in educating the masses and getting back to the main point– the cables. Unfortunately Operation: Leakspin requires more time and more effort than Operation: Payback which is why it is hard to get the masses of Anonymous to change course. Still we can only hope and support Wikileaks through our actions.
Please continue to submit articles, information, and cables to reddit as well as Twitter. It may seem like a big deal to us, but the truth is many people really don’t understand what is going on. They watch the news and see Assange and hear about the DDoS attacks but they never get what it is all about and they never hear the cables.
Operation Payback Spokesman Leaves Name in PR Meta Data
The rogue hacker group Anonymous, which has been making headlines for their repeated DDoS attacks dubbed Operation Payback, issued a press release. The most interesting piece of information int the release, though, was the name of the text’s author, which was present in the PDF’s meta data…
https://www.infosecisland.com/blogview/10196-Operation-Payback-Spokesman-Leaves-Name-in-PR-Meta-Data.html
okay guys, take this: here are people out on the planet wich have time, infrastructure, knowledge and the will to do something and help. but keep in mind, some of us have to stay at least in a grey zone.
so i know you need me, but i dunno how to help! i know i have no solution BUT we need something for people to copy what so every. gimme me a how to of what to do. make it easy for people to adopt it.
i know you will find s solution for that kind of “low level support”, if you do start spread it! please
I squeezed your post into a graphic for those prone to TL;DR 🙂
one of the many Anon servers [currently UP at 18:30 GMT 00 ]
http://pastebin.com/raw.php?i=9rRmf6W5
Thousands of people individually choosing to act to make the world a better place (according to their values)… is that anarchy? Sounds like Big Society to me, throwing open it’s windows and declaring it’s as mad as hell (and it isn’t going to take it any more).
CORRECTION: in your text says 18th of November, when it should say DECEMBER. 😉
You’re right, changing it right now, thanks! 🙂
Да, неплохо поработали, в другой раз дядя СЭМ будет знать что можно, а что нельзя делать.
Village Stavropol region north Caucasus, Russia
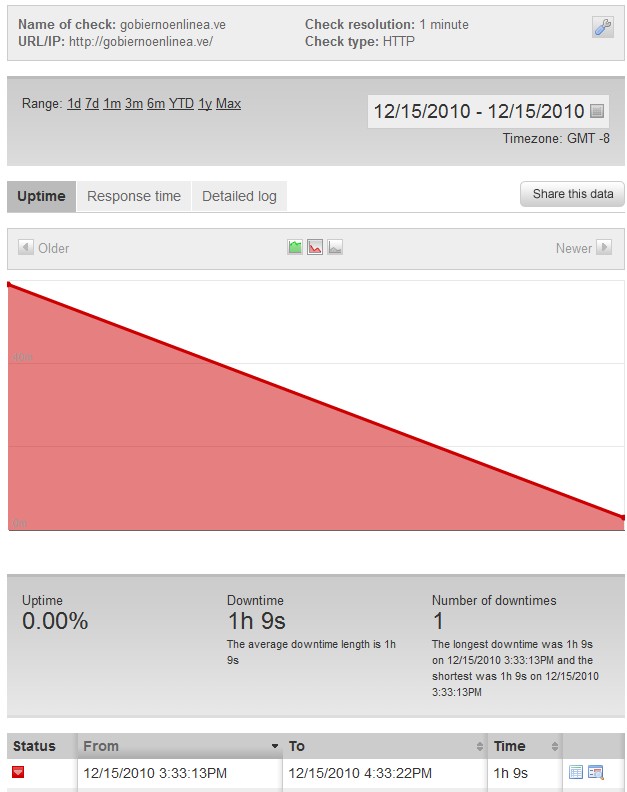
They are now DDOSing http://www.gobiernoenlinea.ve and its down as I write this…..
There is an ongoing attack on the Spanish government http://congreso.es since yesterday. The web has been up and down since then,
The web of the new “sustainability law” has been under heavy attack today. This law was due to be passed today at 15:00 GMT+1, but the voting has been delayed until 21:00 under very strong controversy.
the intranet of the congress was put down as well….and finally the law was not aproved…
Thanks for Sharing this fantastic blog. I really enjoyed it and get to learn many important things. You should keep writing and spreading this type of informational blog.