Some weeks ago we unveiled an attack that affected hundreds of restaurants in the United States using a malware called PunkeyPOS. Something that we did not disclose is how we discovered PunkeyPOS: it turns out that we’ve actually been investigating a series of PoS (Point of Sale) attacks that have also affected hundreds of bars, restaurants and stores in the US. While we were analyzing one of these attacked systems, it was attacked by yet another cybergang using PunkeyPOS. In this article we are going to discuss this attack that we are still investigating that uses a PoS malware called PosCardStealer.
PosCardStealer: A New PoS Attack
The first attack we were able to analyze took place September 30, 2015 and affected 30 PoS systems. The malware was installed using PowerShell, a popular Windows tool. With this tool the file (MD5: 0B4F921CF2537FCED9CAACA179F6DFF4) was executed, with an internal date of creation for two days before (28/09/2015 17:07:59) and compiled with C++ visuals.
The installer’s job is to infect the system with malware that is specifically designed for PoS systems. To do this, it uses different techniques in function with the PoS software installed on the system. In concrete, it looks for brain.exe (pertaining to Dinerware) and scpwin.exe processes, and installs the malware as follows depending on which of the two it finds:
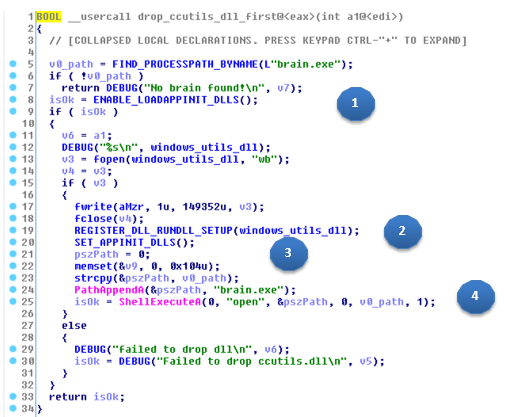
– brain.exe: In this case it will make the actual Dinerware software process load PosCardStealer. To do this, it modifies a couple of registry keys from Windows.
It carries out the following steps:
1-Enables the automatic load of DLLs by calling ENABLE_LOADAPPINIT_DLLS (0x004017A0) and modifies the following registry key:
SOFTWARE\Microsoft\Windows NT\CurrentVersion\Windows LoadAppInit_DLLs = 1
2-If the previous key is modified successfully, it will install PosCardStealer in:
C:\Windows\utils.dll
3-Afterwards, it calls SET_APPINIT_DLLS (0x00401850) to add the new DLL path to the registry so that it loads automatically:
SOFTWARE\Microsoft\Windows NT\CurrentVersion\Windows AppInit_DLLs = C:\Windows\utils.dll
4-Finally, it executes the PoS software once again (“brain.exe”); which will load the DLL that was just installed.
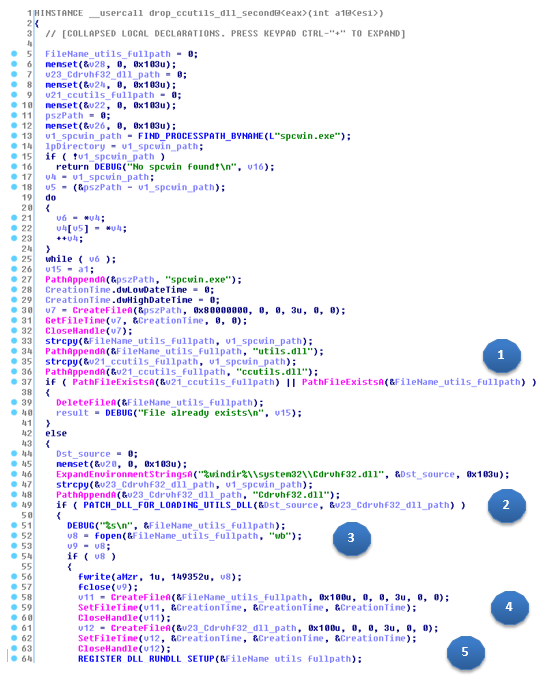
- scpwin.exe: in this situation it will use a technique known as “DLL hijacking”. After finding scpwin.exe in the attacked system, it will copy the “Cdrvhf32.dll” (legitimate) DLL from the Windows system directory to the folder where the same application can be found. Then, it will patch (modify) the copied DLL so that PosCardStealer (utils.dll) can load from there.
In the following screenshot we can see the pseudocode that is in charge of performing this action:
Now, the routine carries out the following steps:
- It makes sure that the files “utils.dll” or “ccutils.dll” do not exist in the PoS software folder
- If the DLLs are not found, it patches the “%windir%\system32\Cdrvhf32.dll” and copies the “spcwin.exe” folder.
- If it successfully patches the “Cdrvhf32.dll” library it will also copy the malicious “utils.dll” DLL code to the “spcwin.exe” folder. The patched library “Cdrvhf32.dll” has the same features as the original, in addition it will execute “extra” code: will load the malicious library “utils.dll”
- Following this, the date-of-creation/access/modification of the libraries “cdrvhf32.dll” and “utils.dll” will be updated to match the date of “spcwin.exe”
- Lastly, it will execute “export” _Setup@16 from the “utils.dll” library from the REGISTER_DLL_RUNDLL_SETUP routine.
This variant of PosCardStealer (MD5: 81060E53D233711507F60C446418AFC6) is compiled in Visual C++ and has the following internal date: 27/09/2015 12:26:09. All of this –plus some other evidence the lab has- points out that these analyzed malware samples were created specifically to attack these victims.
A common characteristic in all of the attacked equipment is that the LogMeIn software was installed. This software is extremely popular and can be used to remotely access systems. In the case of PoS systems, it can be used by the same business that provides PoS systems to restaurants in order to perform updates, maintenance, etc.
LogMeIn: Remote Attacks
Although the use of LogMeIn could be anecdotal, in this instance we have found out that it was relevant: barely a month and a half after this attack was carried out, a new attack was performed using LogMeIn. In this case not only the 30 previously compromised PoS were affected, hundreds of additional ones were also attacked. All of them were in the United States and they mainly belong to restaurants and bars.
In this new attack they used the Multigrain malware, that we analyzed here. The attack began November 13th at 22:09 (GMT) and it only needed 10 minutes to infect all of its victims. This was the process that was used to perform the infection:
- Connect to the PoS using LogMeIn
- Use LogMeIn to download an executable (wme.exe, MD5: A0973ADAF99975C1EB12CC1E333D302F, a variant of Multigrain).
- Execute a script through LogMeIn. This script calls cmd.exe that executes wme.exe.
14 hours later, an isolated attack is launched against one of the PoS. This attack installs a new version of Multigrain (MD5: A3B944454729EA13AD847D01FFAC556A). After half an hour –we suppose that this time lapse is to verify that everything functioned correctly – they replicate the attack against all of their victims, automatically, so that all of the machines will be infected with the new version of malware after only 10 minutes.
These systems were compromised for months. When the people responsible for the PoS systems realized that they were under attack and cleaned the PoS systems, the attackers were able to pick up where they left off using LogMeIn to install a new variant of Multigrain (MD5: 4C722EA25EC857E1A7E73DE5886F9299).
It should be clarified that the LogMeIn attack is not due to any vulnerability, but due to the fact that the attackers had already compromised the computers and had the necessary credentials to enter the system. We advise LogMeIn users to follow the directions published in this document.
Some Advice for Avoiding Cyberattacks
This type of attack allows you to steal information from thousands of credit and debit cards in a fairly simple way. PoS systems are critical and must be protected in the event that it becomes necessary for them to have remote access software installed. All available security measures (two-step verification, restriction of IP addresses of connected devices, etc.) should be enabled. It should be mandatory to have full control of all programs running on these terminals.
Keep in mind that being knowledgeable about your environment is power. The best way to have complete security in your entire IT park is with Adaptive Defense. Make sure to activate the “Lock” mode to prevent the execution of unknown process… this will keep all of your and your customers’ information protected and safe.





1 comment
Hello guys!
My POS terminal is broken ((
What can happen with it? Is it something wrong with cyber security or not?
Please help me. I have this POS system device
http://pos-il.com/