Last week I congratulated Spanish National Police for the fantastic job done that took down a cybercrime gang that was using the known “police virus”, but I already pointed out that this was not going to be the end of this threat, as most likely there were a number of different gangs using the same kind of attacks.
I talked about different evidences that indicated this fact: different techniques within the malware that were not used anymore suddenly appear again (encription of files in the infected computers, for example), how to perform the same actions (like showing the fake police warning screen) were performed in completely different ways, showing that they were different projects, or how we are still seeing new attacks performed on a daily basis.
Anyway I decided to pull the thread and look for some figures to see if they are coherent with the previously described evidences. In most of the cases, computers get infected via the infamous “exploit kits”, tools used by cybercriminals to install different malware just visiting a compromised web site without user intervention. To achieve this, exploit kits use different security holes in software installed in the computer, most of them based on Java or Adobe, as this is very popular software with hundreds of millions of users and with -sadly- many security holes. To make it worst, many users do not bother updating that software, which is like having an open door in your computer with a big sign saying “please infect me”. In short: infecting computers is child’s play in many cases.
This is why some months ago we deployed a new technology in Panda Cloud Antivirus that allows to stop infection attempts that try to use this kind of vulnerabilities (even when it is an unknown vulnerability) and furthermore it sends information to our cloud with data of the malware file that was trying to infect the system.
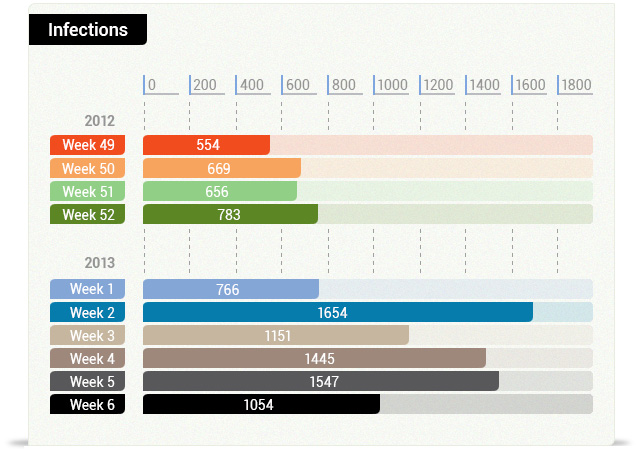
Out of all the data, I have extracted a couple of different families that belong to the police virus to see how many infections have we stopped since December 2012 until mid February 2013. In other words, we are talking about Panda Cloud Antivirus users that while on the Internet were attacked with an exploit they had no protection for (his software wasn’t updated, most of them Java related) and which aim was to infect them with any of these particular 2 families of the police virus.
The Russian head of the cybercriminal gang was arrested in Dubai last December. If this was really the only gang behind these attacks, as we have seen in some media, the number should have dropped considerably. However, this is the result:
As we can see, the number of blocked infections is not going down, it has increased by 2! This is a proof that shows how we will have to deal with this police virus for a long time, war is not over yet (as usual ;))
These 2 families, as well as many others, are detected by Panda with the name Trj/Ransom.AB. If you have been already infected and need some help, our Technical Support team have the following instructions that work really well to solve all your problems.
Finally, some advices to avoid becoming a victim of these cybercriminal gangs:
– Update. All installed software. From the operating system to any other software you have in your computer. Don’t be lazy, it is worth it 😉
– Uninstall any Java plugin in the browser. You don’t need it and you get rid of a HUGE risk. Not only this, unless you need Java to run some local application in your computer, remove it completely. I did this long time ago. An ounce of prevention is worth a pound of cure.






3 comments