Social engineering is a tactic that cybercriminals use to manipulate people into revealing private information or sharing sensitive data. If you’ve ever gotten an unexpected phone call or email from someone asking for your account information, social security number or other personal information, you might have been the target of a social engineering attack.
Attackers who use social engineering don’t need to hack into databases or breakthrough cybersecurity tools. Instead, they convince targets to willingly hand over sensitive information by imitating trustworthy companies or offering fake products. These scammers can target anything from credit card numbers and bank account information to secured files and devices.
Social engineering can take many forms and isn’t always easy to spot. Fortunately, there are multiple strategies you can use to identify potential scams and protect yourself from future attacks.
How Does Social Engineering Work?
Social engineering works by tricking people into revealing sensitive information or providing access to a personal device or account. Scammers typically pose as someone you can trust and contact you with a request for information or directions for accessing a website or file. For example, this could look like an email from a company urging you to download an attachment or a call from tech support requesting login information.
These messages look convincing and can be difficult to distinguish from genuine requests. Scammers often research a company or individual in advance to learn as much about them as possible. Once they have more information, they can personalize their messages based on the target’s affiliations or position within a company.
If the target falls for the scam, they might be prompted to send account information, input their login credentials into a fraudulent site or unknowingly download malware onto their device.
Common Types of Social Engineering Attacks
There are numerous methods scammers can use to perform social engineering attacks. Here are the four most common types:
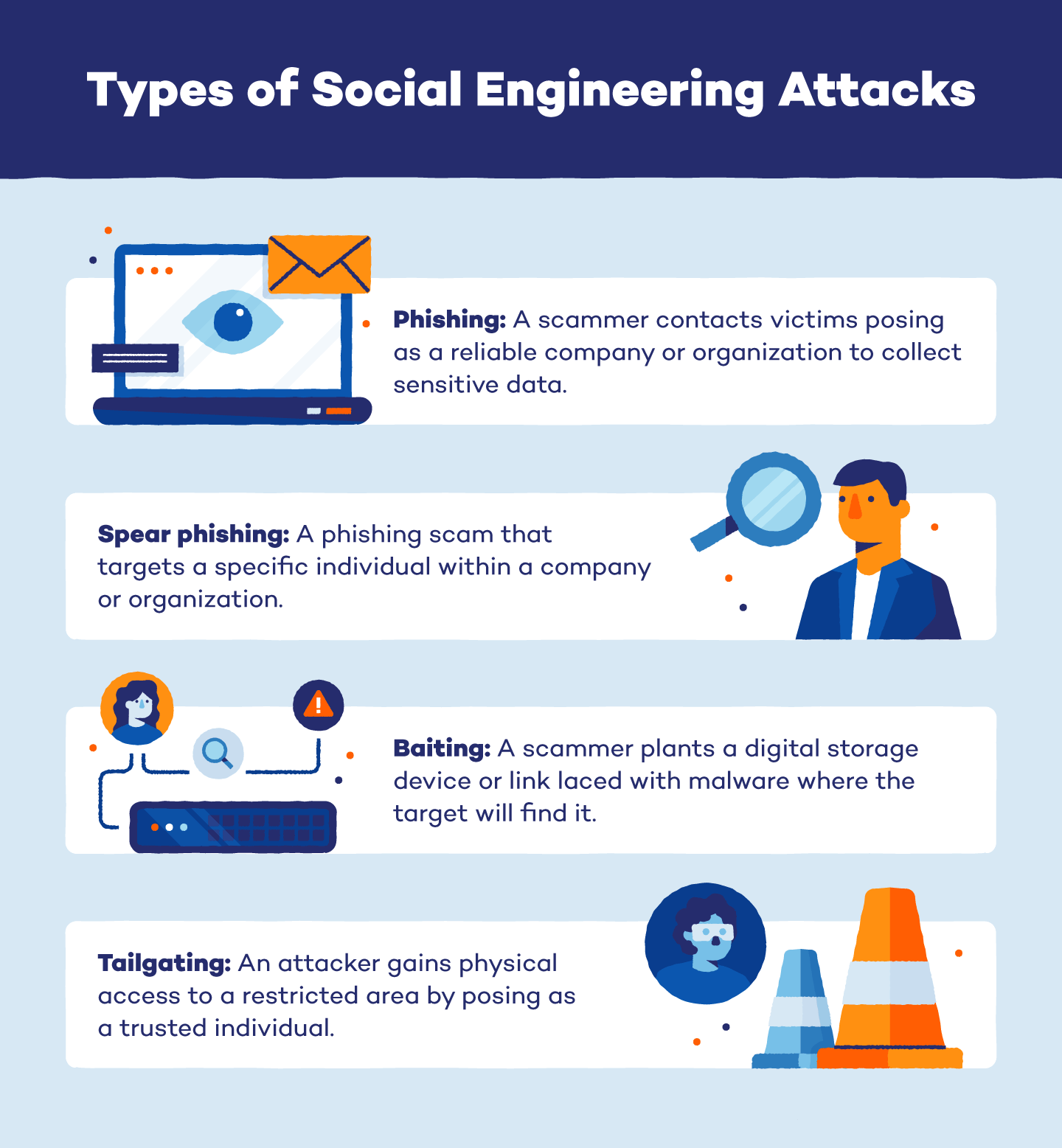
Phishing
Phishing is one of the most common types of social engineering scams. To perform this attack, an individual poses as a reputable company or organization and sends targets an email requesting access to login credentials, credit card information or other confidential data.
Attackers may ask for information directly or prompt users to click on a link that leads to a fraudulent website. Once there, the website prompts the user to enter login credentials or other personal information.
Scammers can also take advantage of other forms of communication to execute phishing attacks. “Smishing” refers to phishing messages sent through text, and “vishing” refers to phone calls or voice messages from scammers posing as a reliable source. These phishing messages typically include a false sense of urgency to trick targets into acting quickly.
Spear Phishing
Spear phishing is a type of phishing attack that targets an individual in a company or organization. Instead of sending out a mass email or message, an attacker chooses one employee to send a personalized request for information. These messages often convince the target that they have a relationship with the sender, making them more likely to share sensitive information or data.
Baiting
While the end goal is the same, baiting works slightly differently than phishing attacks. Instead of sending requests for information, scammers plant ads or hardware that lure targets into accessing malicious websites or downloading malware. For example, an attacker might create a tempting ad that looks like it leads to a product page. However, when the target clicks on it, the link downloads an application infected with malware.
Planting physical hardware is another popular method for baiting scams. To do this, scammers leave a flash drive or other storage device in a location where targets will easily see it. When the victim plugs it into their computer, it infects the device with malware.
Tailgaiting
Tailgaiting is a physical attack where a person poses as an employee or other trusted individual to gain access to a restricted area. This could look like a janitor who asks you to hold the door open or a new employee who lost their key card. Once they have access, the attacker seeks out company records, documents or other restricted information.
Examples of Social Engineering Attacks
Attackers aim to be as convincing as possible, so social engineering attacks can be difficult to identify. Read through the following real-life examples to better understand what a social engineering attack could look like.
Email Phishing Scam Targeting Google and Facebook
One of the most well-known instances of a social engineering attack happened between 2013 and 2015, when a group of attackers used spear phishing to scam Google and Facebook out of $100 million.

The group, led by Evaldas Rimasauskas, created a fake computer manufacturing company nearly identical to Google and Facebook’s legitimate supplier. They then sent specific employees email invoices that instructed them to wire money into a bank account that the scammers controlled. Because the invoices included goods and services the legitimate company had actually provided and the senders seemed trustworthy, the group was able to convince employees to send $100 million over the two-year period.
Social Security Scam
In 2018, the Federal Trade Commission began receiving multiple reports of calls from scammers claiming to work for the Social Security Administration. During these phone calls, scammers would pose as employees and ask victims to confirm their social security numbers. They attempted to make the calls more convincing by explaining that a computer problem had caused an internal issue.
Identity theft through social engineering attacks is an ongoing issue. The social security Administration urges people never to give out social security numbers over the phone if they receive a suspicious call.
Signs of an Attack
Social engineering attacks are quickly becoming more convincing and difficult to detect. Fortunately, a few telltale signs can help you identify an attack before you become a victim.
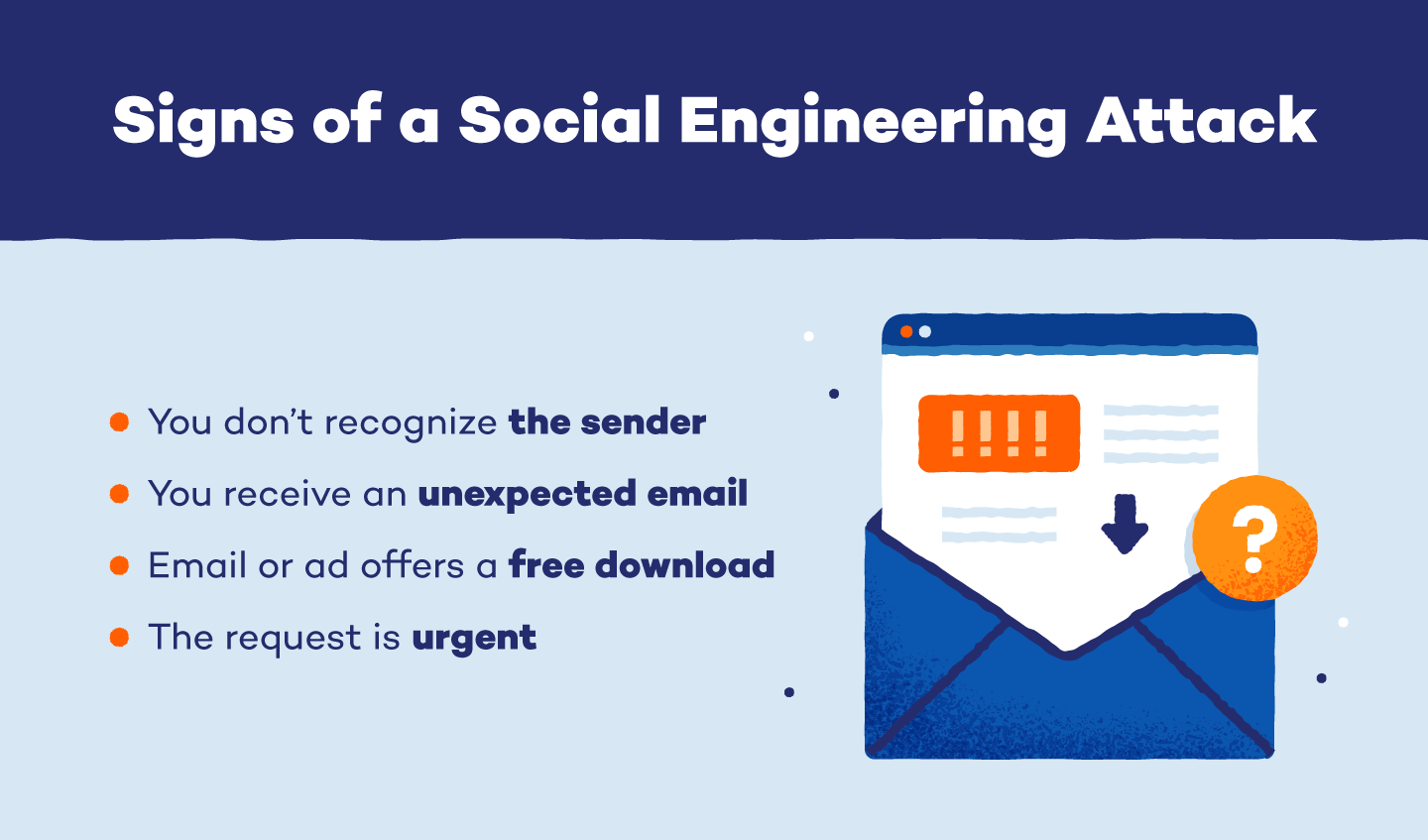
You Don’t Recognize the Sender
Receiving an email or message from someone you don’t recognize isn’t always a sign of a social engineering attack, but you should proceed cautiously. If the sender claims to work at your company or organization, verify their identity before responding or clicking any links.
Unexpected Emails
If you receive an unexpected email from a coworker or company that you don’t normally correspond with, it could be a scammer. This is especially likely if the message requests login information or other sensitive data and expresses a sense of urgency. Scammers often use this method to trick employees into sending information out of fear of angering their boss. If this happens to you, avoid responding to the email or opening any attachments until you can follow up with your boss or coworker in person.
Free Download Offers
Social engineering scammers often entice targets to click on links laced with malware by offering a free downloadable product. These offers generally come through email or an online ad and offer free apps, music, e-books or other digital products. Download buttons can even pop up in online articles or next to legitimate links to trick users into clicking.
You Feel Pressured by Urgency
A strong sense of urgency is one of the most common traits of a social engineering attack. Scammers don’t want to give you time to think about the legitimacy of their request, so they may say that there’s an emergency or deadline and they need your information as soon as possible. Requests like this can be especially hard to resist if the sender is posing as an employer, financial institution or other important organization. However, it’s crucial to fact-check unexpected urgent requests before providing any information.
How to Protect Yourself
Once you know the signs of a social engineering attack, consider taking the following steps to protect yourself from future attacks.
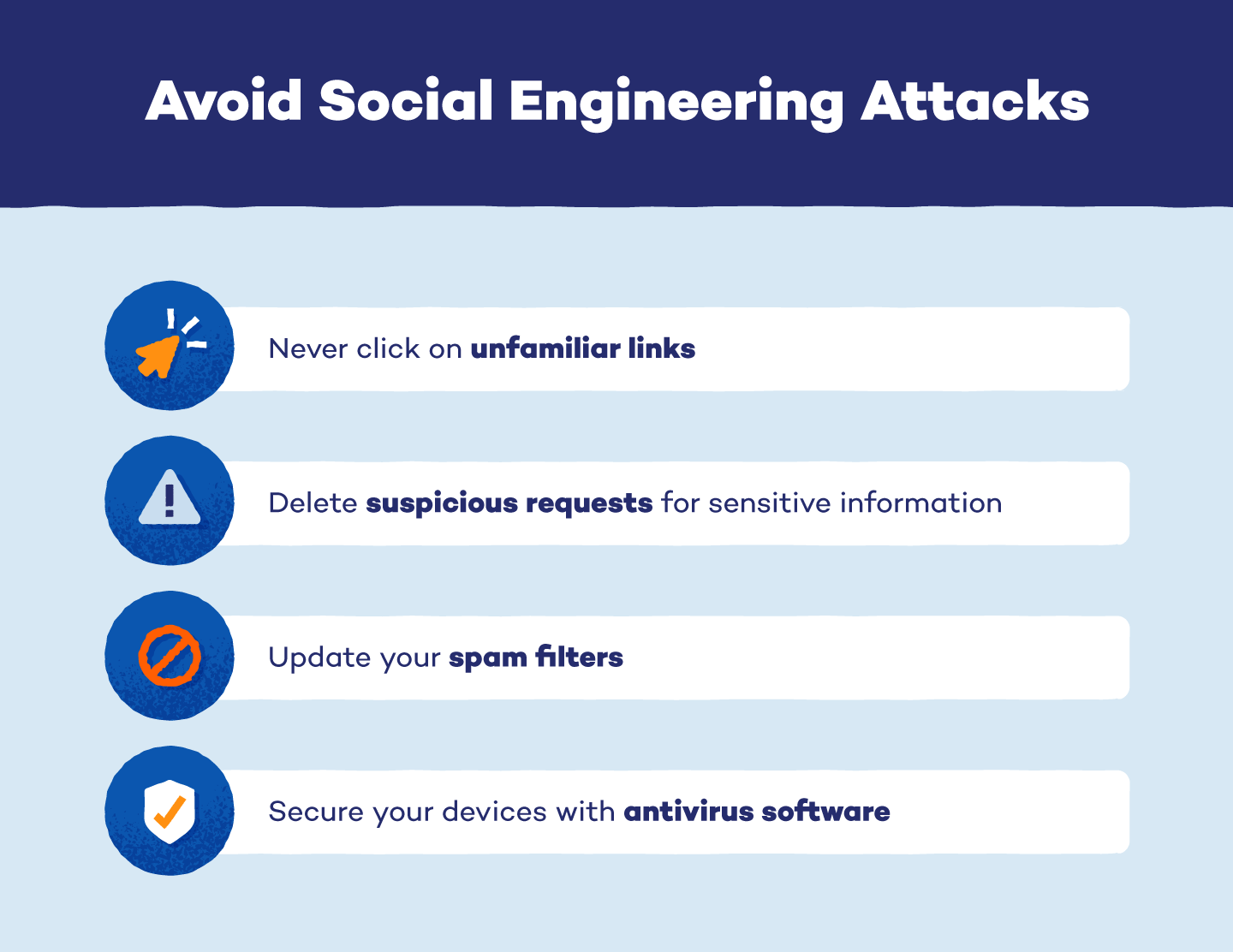
Never Click Unfamiliar Links
Never click on a link for a free download from an ad or unsolicited email. Scammers frequently add malicious links to emails or online ads to convince victims to download malware onto their devices. If you receive a suspicious email offer or see an ad that seems too good to be true, it’s likely a scam. Clicking on the provided link without verifying its authenticity could expose your device to malware or compromise sensitive information.
Delete Suspicious Requests for Information or Assistance
If you receive a request for information from a source you can’t verify, delete it from your inbox without opening any links or attachments. This ensures that you won’t accidentally open it later or pass it on to someone else.
Update Spam Filters
All email programs offer spam filters to prevent fraudulent or unwanted messages from making it to your inbox. If you haven’t checked your spam filter setting in a while, go to your email settings and ensure that your filter is enabled and updated. Most basic spam filters also allow you to create personalized filters and block specific senders.
Secure Your Devices
Cybersecurity tools may not be able to prevent social engineering scams, but they can help protect your device from malware if you fall victim to an attack. Antivirus software is a great tool to add to your devices to protect against viruses and scan for malware. You should also create strong, unique passwords for your online accounts and update your login credentials periodically to ensure that your online accounts are as secure as possible.
Social engineering attacks are especially dangerous because they bypass traditional antivirus software and cybersecurity tools. However, as long as you remain vigilant and take the proper precautions, you can reduce your risk of falling victim to an attack.
For more ways to secure your devices and protect your online activity, check out our antivirus tools and VPN for Windows and Android.




