These days, the most talked-about story in the security world is the discovery of a new Java vulnerability that could allow attackers to spread malware.
On January 10, a researcher going by the name of @kafeine posted an article on his Twitter account explaining that several exploit kits such as BlackHole, Cool EK, Nuclear Pack and RedKit were taking advantage of a new vulnerability discovered in the latest Java version (Java 7 Update 10) to install the infamous “Police Virus” and other malware without users having to open any files. Simply visiting certain websites was enough to trigger the infection. The hackers called this new exploit a “New Year’s gift”.
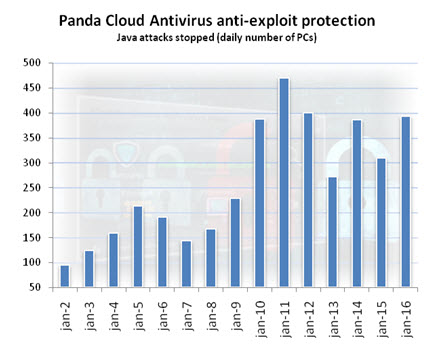
The news spread like wildfire and was covered by a large number of publications, including PCMag and KrebsonSecurity, which advised users to disable Java to prevent exploitation. One day later, a Metasploit module was developed to target this flaw. Then, it was only a matter of time until the new exploit was incorporated into other popular exploit packs. This was further confirmed by our Collective Intelligence technologies, which detected a spike in attacks that took advantage of Java vulnerabilities.
The most important thing: Does Panda Cloud Antivirus protect you against the latest Java vulnerability? (CVE-2013-0422)
Yes, it does. Not only are users of Panda Cloud Antivirus 2.1 protected against this vulnerability now, but they have been protected even before the flaw was discovered last week.
Let’s take a closer look.
Some technical information about the exploit: How does it exactly work? — Warning – What follows may be extremely boring for non-geeks —
[Geek mode: ON] 😉
This vulnerability has been extensively documented. In short, the exploit takes advantage of two security flaws: The first flaw stems from the fact that it is possible to obtain references to restricted classes.
The second one allows it to invoke class constructors by using the reflection API included in Java 1.7.
Without going into any more details, the most important thing is to note that the flaw stems from the Java Virtual Machine Security Manager.
On January 14, Oracle released a patch for this vulnerability in version 1.7.0_11. Surprisingly however, it also decided to increase the default security level for Java applets and Web start applications from Medium to High. With this setting, the user is always warned before any unsigned application is run to prevent silent exploitation. In other words, the ‘Java patient’ left the operating room with a big, ugly scar on his forehead for everyone to see…
Given the importance of the measure, it is surprising that the decision was made so quickly (in theory, between January 10 and 14, the dates when the vulnerability was first discovered and fixed respectively). It can then be concluded that what actually triggered the decision was something else besides the vulnerability.
It is yet to be seen how this change to the default Java settings will affect future attacks, although it seems that the use of Java vulnerabilities in exploit kits will decrease. Only time will tell. By the moment, less than 24 hours after Oracle released new version, there were already people selling an exploit for a different and apparently still-unpatched zero-day vulnerability in Java.
[Geek mode: OFF]
How come I was already protected by Panda Cloud Antivirus even before the vulnerability was first discovered?
The key to detect as-yet-unknown exploits is to use heuristic technologies with powerful detection capabilities and a near-zero false positive ratio. For this purpose, the new anti-exploit protection included in Panda Cloud Antivirus 2.1 analyzes how exploits behave instead of their morphology.
Panda Cloud Antivirus uses multiple sensors to send Collective Intelligence information about the behavior of suspicious files that try to exploit 0-day vulnerabilities to infect PCs in the Panda Community. This information allows us to constantly update the proactive technologies included in our product (via hot updates from the Cloud) to adapt to the ever-changing threat landscape.
Panda Cloud Antivirus detects and neutralizes this type of malware before it has been identified (and even created), protecting users against new malware variants.




2 comments
Mi codigo de Activacion no Funciona y hace 2 meses lo tengo. instale win 8 pero lo desinstale y tengo ahora el win 7 y me dice que el codigo esta siendo utilizado en otro equipo… que hago?
Hola JuanK,
puedes liberar esta licencia desde tu área:
https://www.cloudantivirus.com/es/myaccount/accountdetail/
Introduce tu código de activación en la zona de “Datos de tus servicios” y pulsa en “liberar”. Cualquier duda, por favor, utiliza el foro de soporte. Al ser un usuario PRO, puedes utilizar el foro VIP en tu idioma: http://www.cloudantivirus.com/forum